The entry point for permissions is as follows:
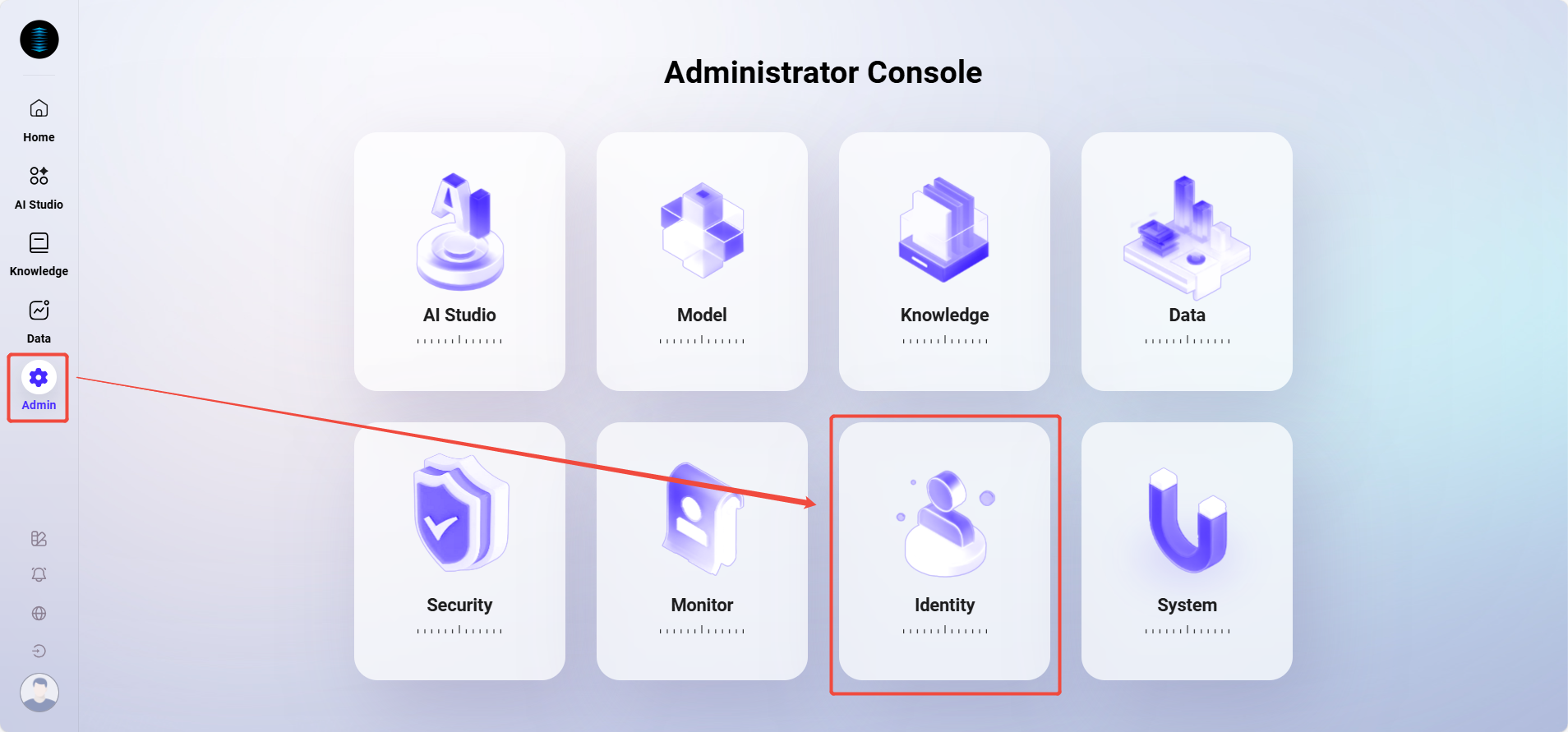
User Management
How to add a new user?
The steps to add a new user are as follows:
-
Go to the Management > Permissions > User Management page.
-
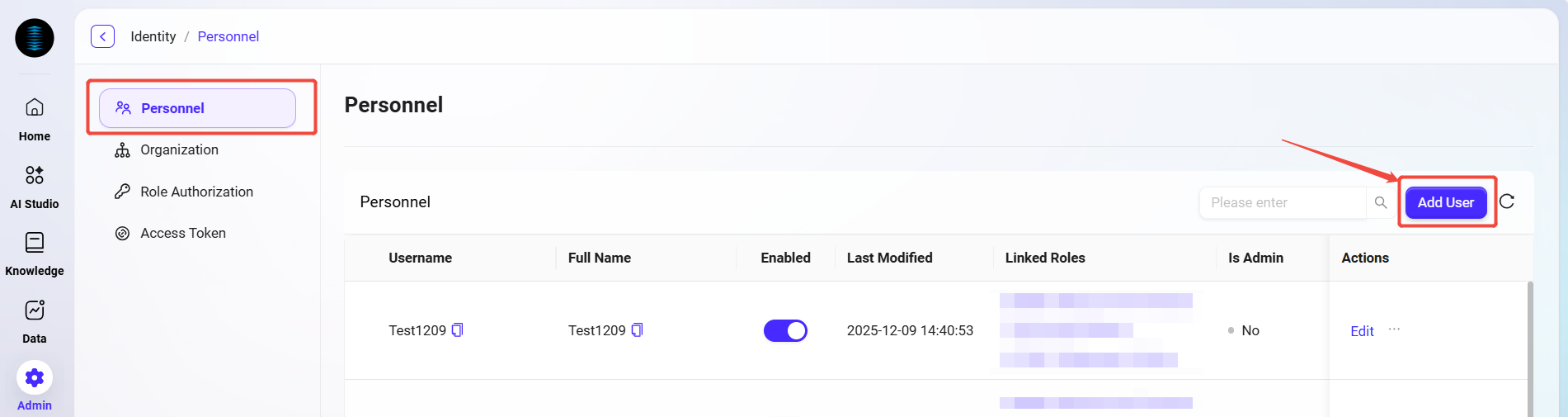
Click the Add User button on the right to enter the Add New User page.
-
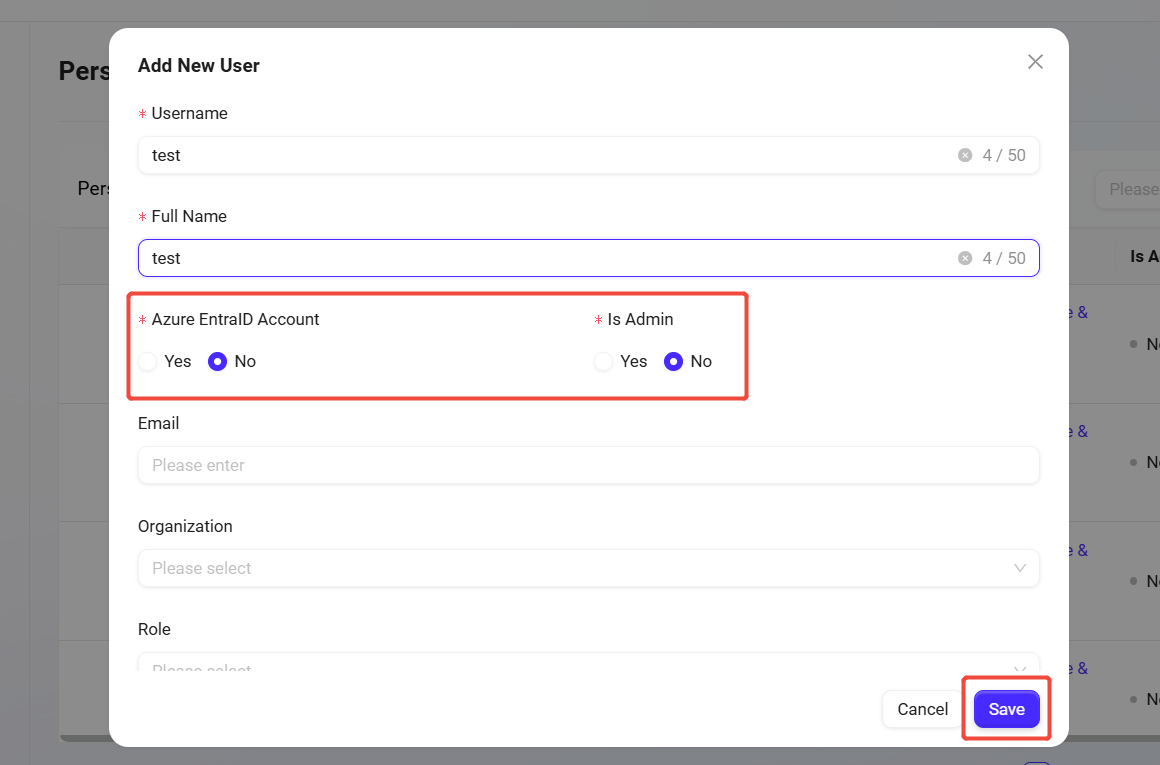
Fill in the user information:
-
Username: Enter the username for the new user (up to 50 characters).
-
Real Name: Enter the user's real name (up to 50 characters).
-
Is Azure EntraID Account: Select whether this is an Azure EntraID account.
-
Is Admin: Choose whether to set this user as an administrator.
-
Other information (such as email, organization, role, etc.) is optional and can be filled in as needed.
-
-
After completing the information, click the Save button to create the new user.
💡 Tip: If you select Azure EntraID for the new user, the email field is required.
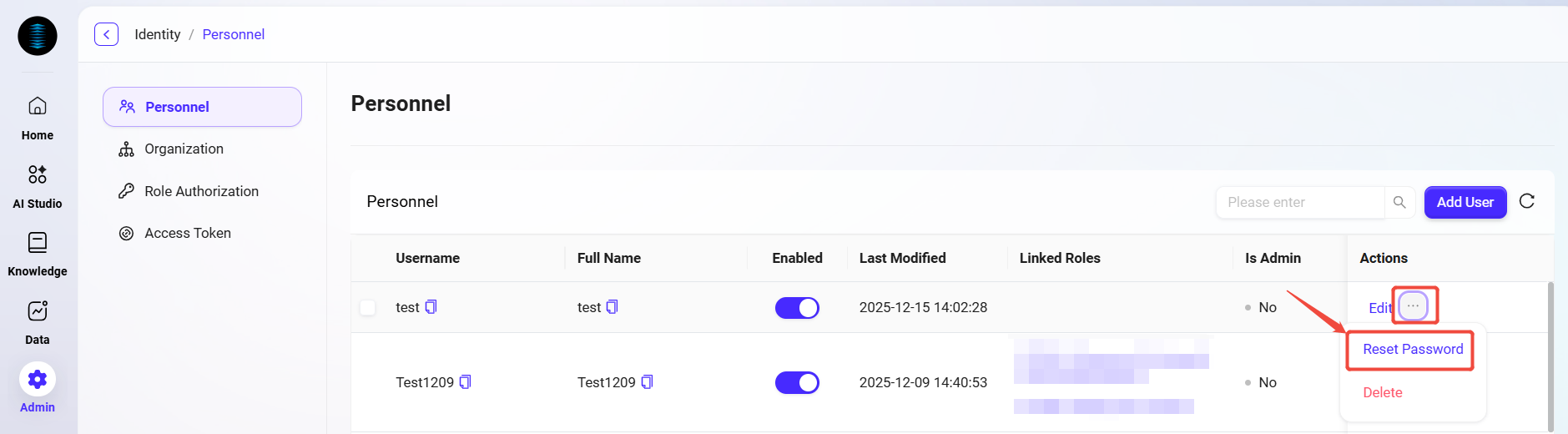
How to change a user's password?
The system supports two ways to change a user's password:
Administrator resets password (for forgotten passwords or initial setup)
The administrator can generate a temporary random password for the user. The user must change the password immediately after logging in with it for the first time.
-
Navigate to Management > Permissions > User Management page.
-
Find the user whose password needs to be reset, click the three dots next to the user, and select Reset Password.
-
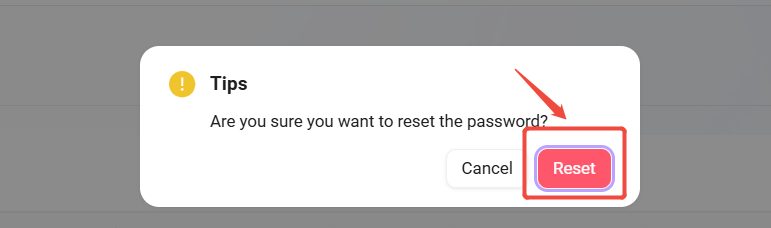
In the pop-up confirmation dialog, click Reset. The system will generate a new random password.
-
Copy the new password and provide it to the user to complete the password reset.
💡 Tip:
After resetting the password, the user must change the password upon first login, thus achieving the purpose of password modification.
Passwords must be at least 10 characters and include uppercase and lowercase letters + numbers + special symbols.
Organization Management
Administrators can manage organizations in the system, including creating, editing, and deleting organizations, and associating users with organizations. Organization management helps efficiently manage various internal teams and external partners.
View Organization List
-
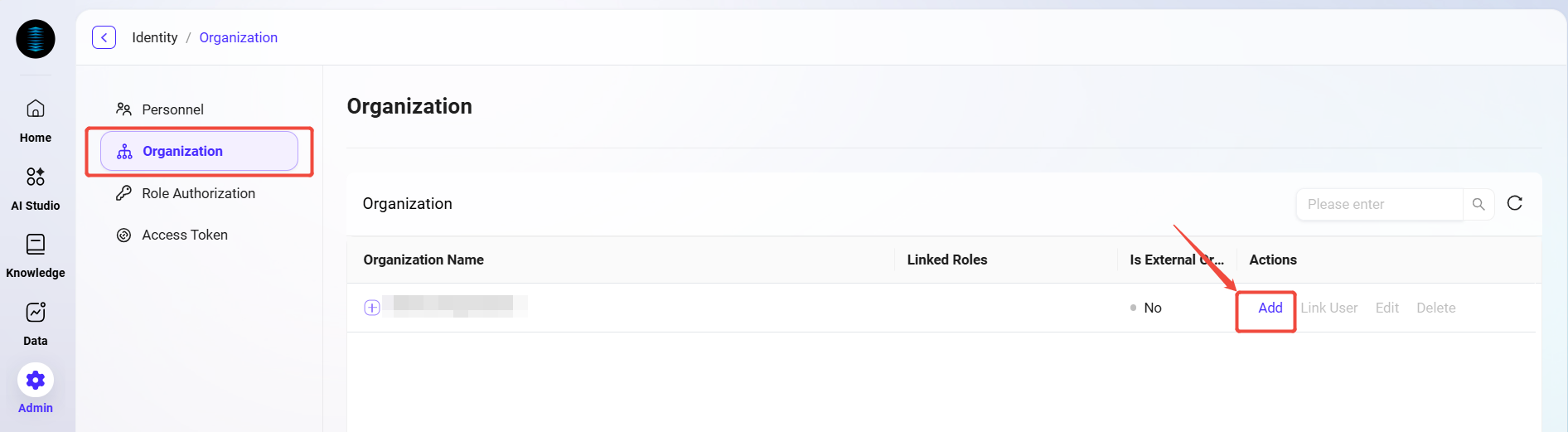
Enter the Organization Management page: Select "Organization Management" in system settings to enter the page.
-
View created organizations: The system displays all existing organization information, including organization name, associated roles, and whether it is an external organization.
-
Each organization has an "Edit" button on the right for administrators to modify the organization, or click the "Delete" button to remove the organization.
-
How to create a new organization?
-
Click the "Add" button: On the Organization Management page, click the "New" button on the right to start creating a new organization.
-
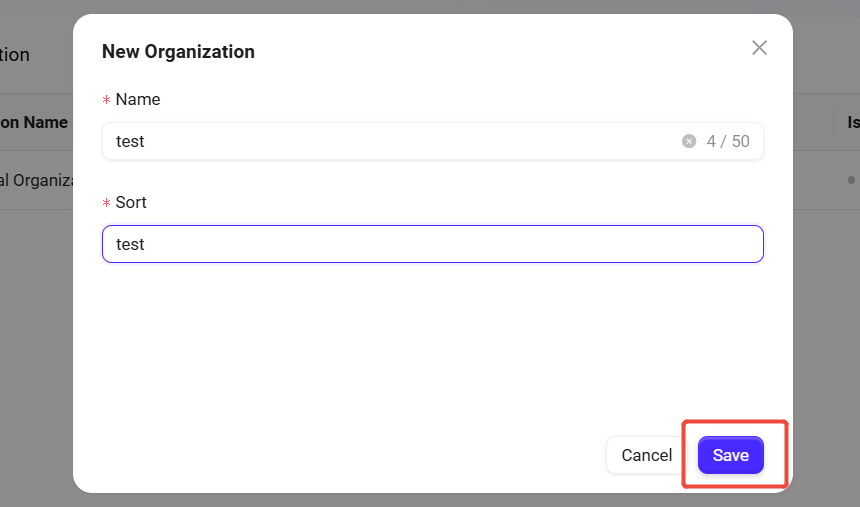
Fill in organization information:
-
Organization Name: Assign a unique name to the organization.
-
Sort Order: Assign a sort number to the organization for easier management.
-
-
Click "Save": After filling in all required information, click the "Save" button to successfully create the new organization.
💡 Tip: It is recommended that the organization hierarchy does not exceed 7 levels.
How to edit an organization?
-
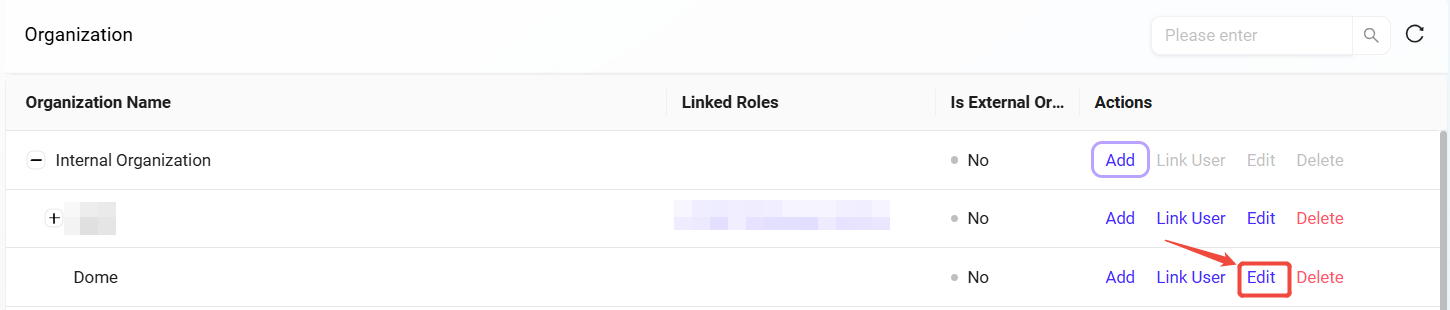
Select the organization to edit: Select the organization to edit from the organization list.
-
Click the "Edit" button: Enter the edit page. The content is the same as when creating a new organization. The administrator can modify the organization's name and sort order.
-
Save changes: After editing, click the "Save" button to update the organization information.
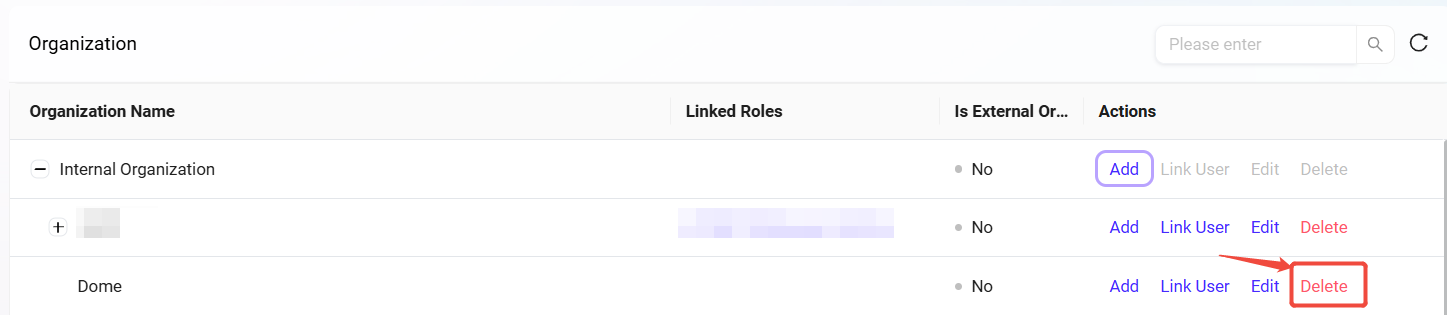
How to delete an organization?
-
Select the organization to delete: Select the organization to delete from the organization list.
-
Click the "Delete" button: After secondary confirmation, the organization can be deleted.
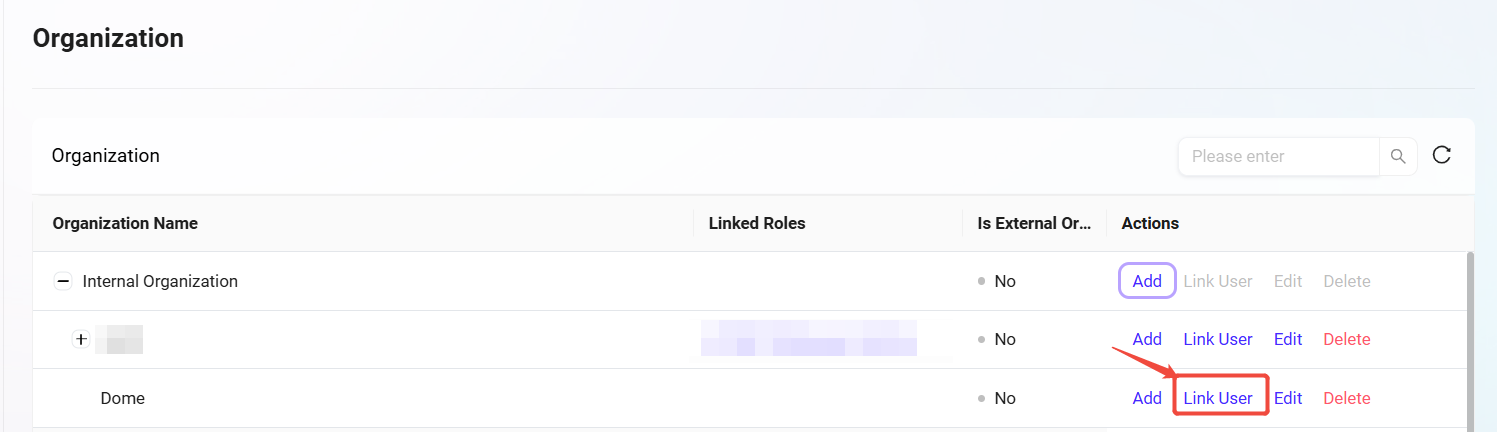
Link User
The steps to add or remove associated users are as follows:
-
Click "Link User": On the Organization Management page, select the organization to associate users with and click the "Link User" button on the right.
-
View Linked user: After entering the Link User page, the administrator can see all users already associated with the organization.
-
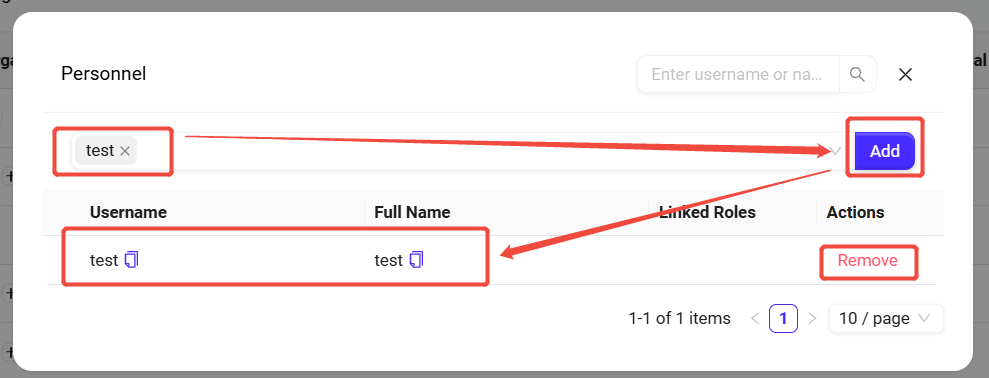
Remove Link User: The administrator can select linked users and click the remove button to remove them from the organization.
-
Add Link User: Select the user to add from the dropdown, click the "Add" button to link the new user with the organization.
Role Authorization
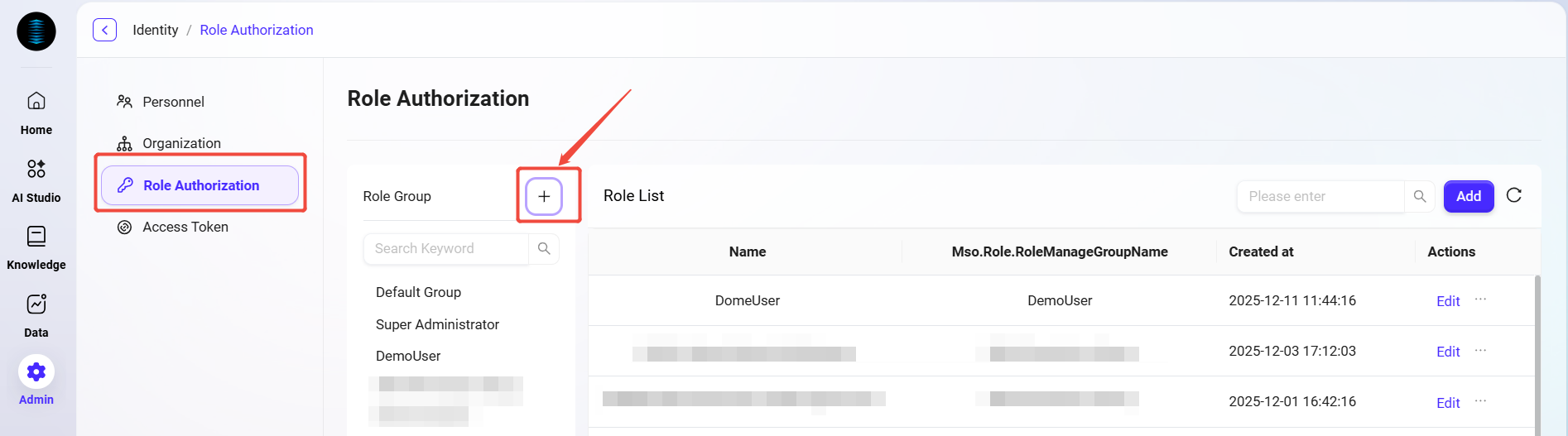
How to create a role group?
In role permission management, administrators can create new role groups. After creating a role group, administrators can create new roles within the group and grant permissions.
-
Navigate to Management > Identity > Role Authorization page.
-
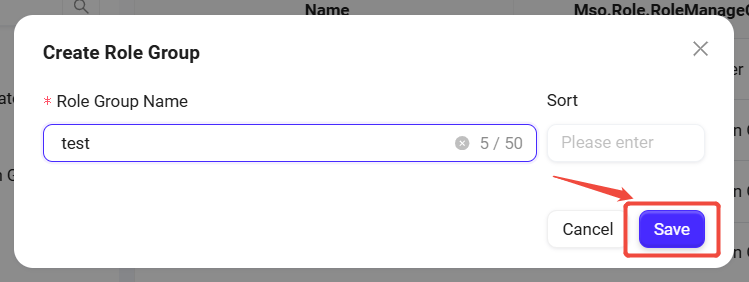
At the top of the role group list on the left, click the + button to create a new role group.
-
In the pop-up window, enter the name and sort order of the role group.
-
Click Save to complete the creation of the role group.
How to add a new role?
-
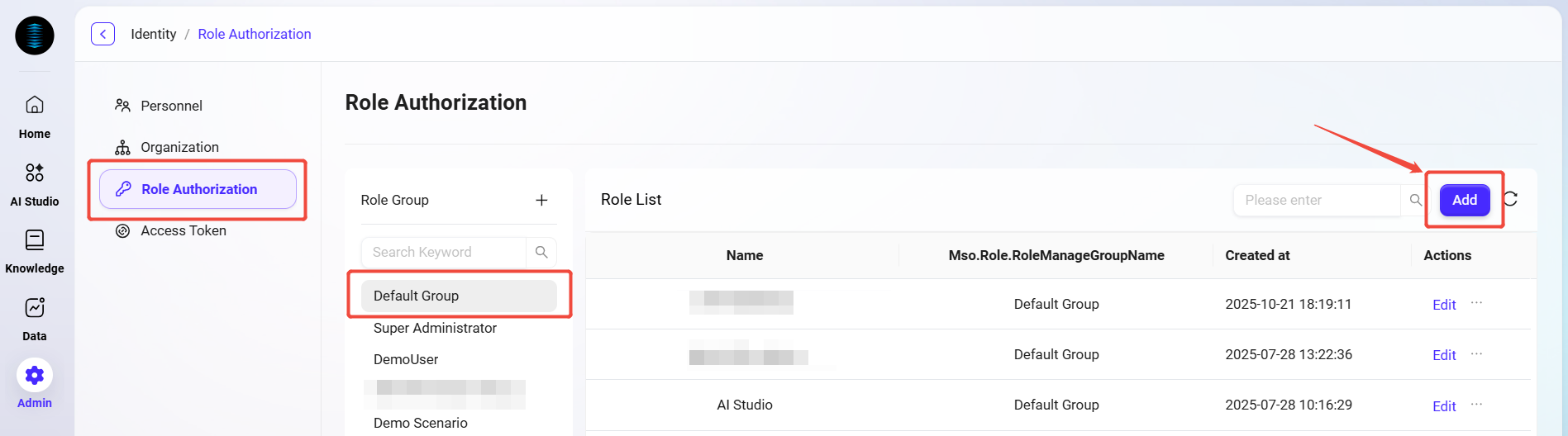
Navigate to Management > Identity > Role Authorization page.
-
Select the role group to create a new role in.
-
On the role group page, click the Add button on the right side of the role list.
-
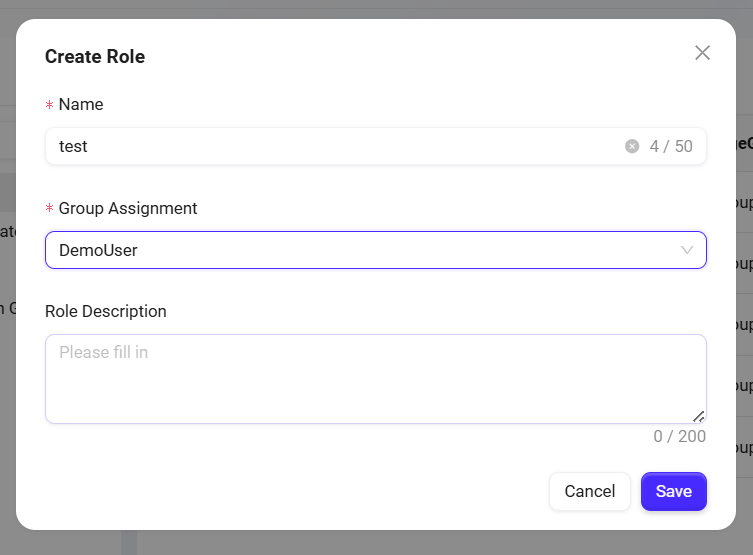
Enter the new role's name, select the group it belongs to, and fill in the role description.
-
Click Save to complete the creation of the new role.
💡 Tip: The character limit for both role name and description is 200 characters. Please pay attention to the limit before proceeding.
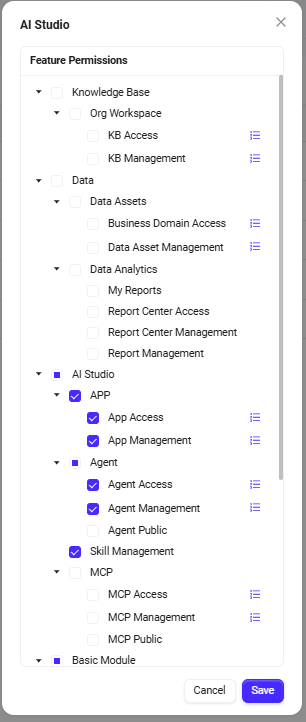
How to grant functional permissions to a role?
Granting functional permissions to a role means specifying what functions the role has.
Steps to grant functional permissions to a role:
-
Navigate to Management > Identity > Role Authorization page.
-
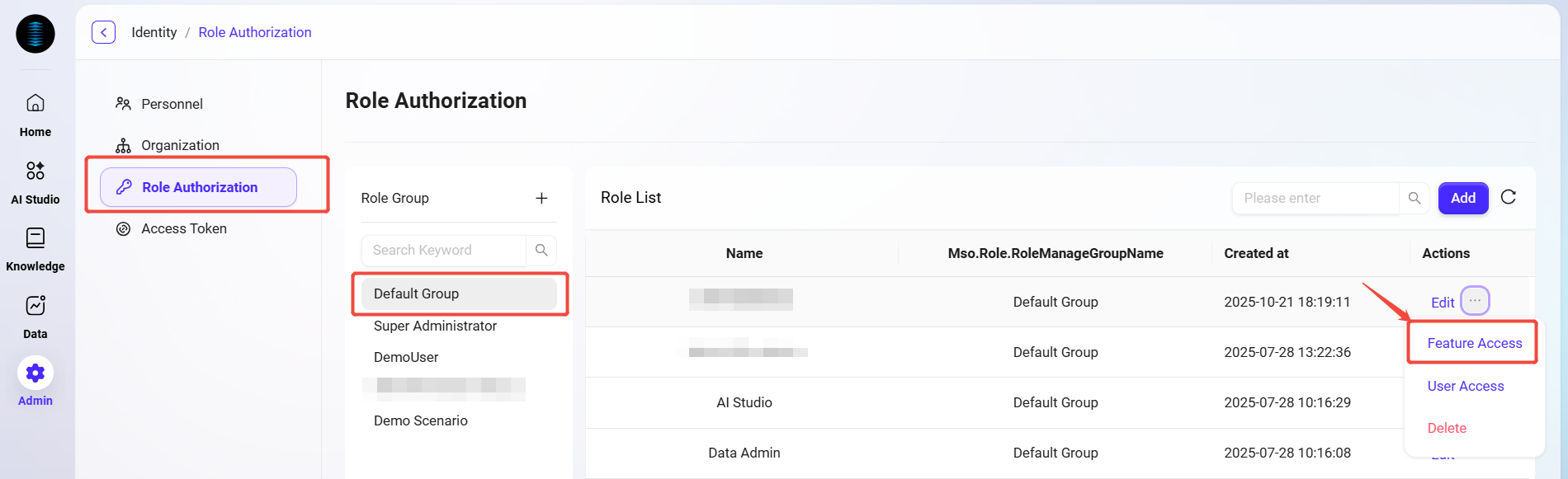
Select the role to grant functional permissions to.
-
Click the Feature Access button next to the role to enter the Feature Permissions page.
-
On the Feature Permissions page, you can grant the following functions to the role:
-
Model Management
-
Model Channel Management
-
App Marketplace
-
Basic Modules
-
Data Analysis
-
Knowledge Base
-
Content Security Management
-
-
After selecting the required functions, click Save to complete the function authorization for the role.
How to grant user permissions to a role?
Granting user permissions to a role means assigning a role to a user.
Steps to grant user permissions to a role:
-
Navigate to Management > Identity > Role Authorization page.
-
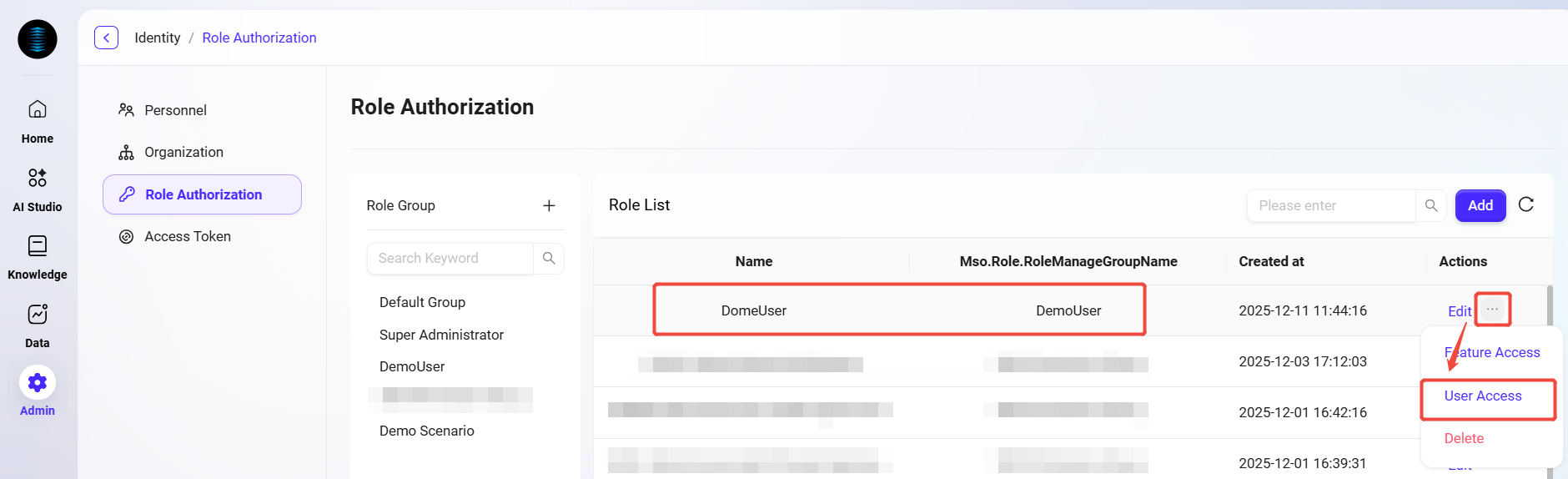
Find the role to authorize and click the User Access button next to the role to enter the Authorization page.
-
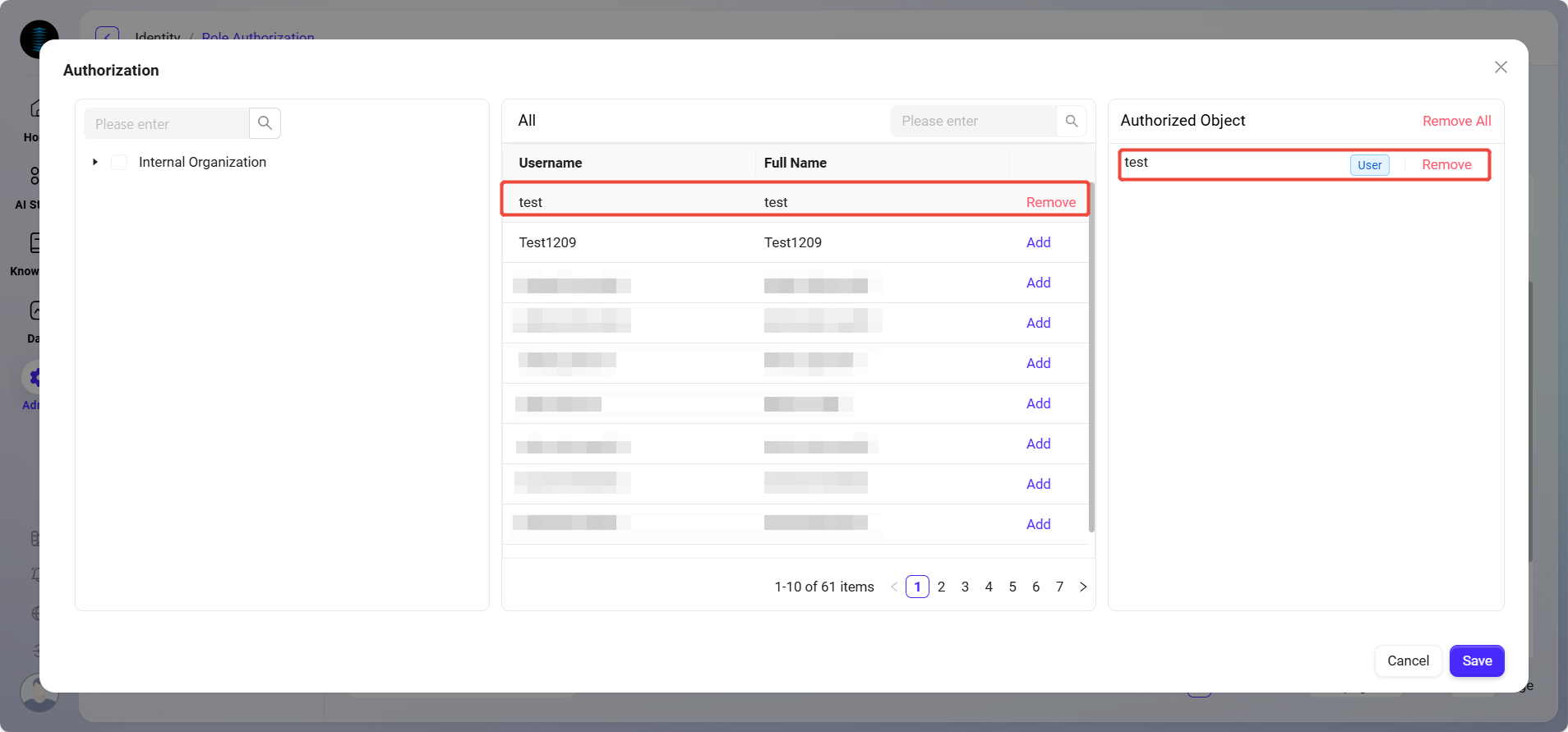
On the Authorization page, find and select the users to authorize by their organization.
-
Successfully selected users will appear in the authorized objects column.
-
After completing the selection, click Save to complete user authorization for the role.
Access Token
💡 Tip: This feature is only supported in V4.1 and above
Access Token is an important new feature module designed to optimize the original API Key generation and usage method. The new version upgrades the previously scattered, resource-bound API Key mechanism to a centralized, user-permission-centric Access Access Token system, achieving higher security and controllability.
In the new system, Access Tokens are strongly associated with user permissions. The access scope, validity period, and management permissions of each token are uniformly controlled by the system, ensuring secure and controllable system resources.
Access Token Supported Scope
Currently, Access Tokens can be used for the following API interfaces:
-
Agent Configuration Query OpenAPI — Supports secure access to Agent-related configurations via token.
-
FAQ List OpenAPI — Supports secure retrieval of FAQ data by external systems.
-
All MCP Server interfaces published by Agent — Ensures all Agent external service access is controlled by the token system.
Access Token Interface Description
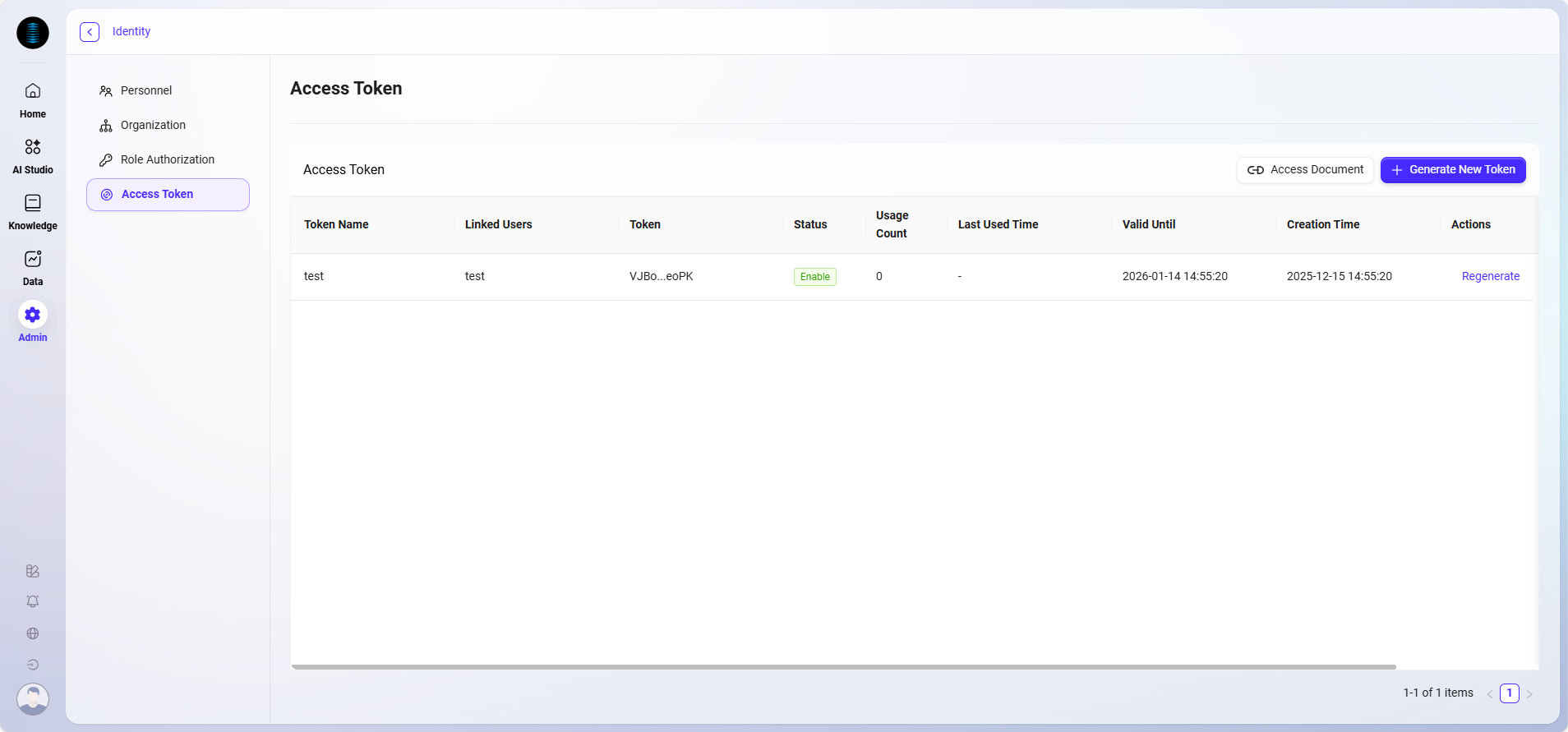
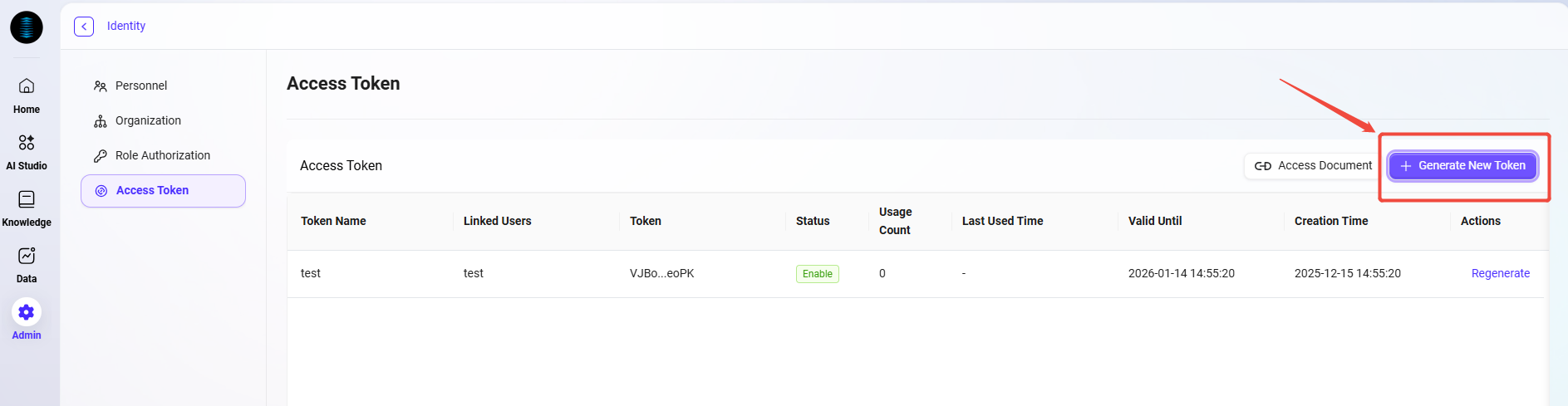
On the "Access Token" page, the system displays all created access tokens in a table, including the following information:
-
Token Name: Custom identifier for the token, used to distinguish different purposes.
-
Linked User: The user bound to the token; the token's access permissions inherit from this user.
-
Token: System-generated Access Token string.
-
Status: Includes Enabled, Disabled, and Expired statuses, clearly reflecting the token's current availability.
-
Usage Count: Tracks the number of times the token has been called, helping administrators monitor usage frequency.
-
Last Used Time: Shows the last time the token was used.
-
Validity Period: Displays the token's validity duration (e.g., 7 days, 30 days, 90 days, or permanent).
-
Valid Time: Records when the token was generated.
-
Actions: Provides a "Regenerate" button to update the token value for security.
Generate New Token
-
Click the "Generate New Token" button at the top right of the page.
-
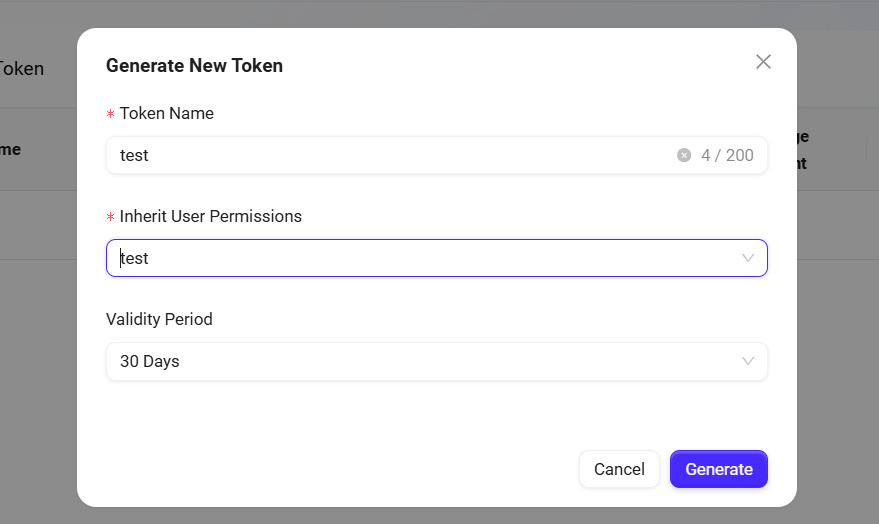
In the pop-up window, fill in the following information:
-
Token Name: Enter a meaningful name for the token for easy identification.
-
Inherit User Permissions: Select the system user whose permissions to inherit; the token will automatically have that user's access scope.
-
Validity Period: Choose from 7 days, 30 days, 90 days, or permanent.
-
-
Click "Generate" to create a new Access Token.
The generated token will immediately appear in the list. Administrators can copy the token for subsequent API access.
Token Usage Instructions
The generated Access Token can be used to call controlled API interfaces (such as Agent, FAQ, MCP Server, etc.). When using, add the token as an authentication credential in the request header, for example:
Authorization: Bearer <Access Token>
This way, the system can verify the visitor's identity and check permissions, ensuring secure and compliant API access.
