The entry point for content security management is shown below:
Sensitive Word Management
The sensitive word management feature helps users effectively control platform content, ensuring compliance, healthiness, and alignment with internal corporate policies or community management standards. By defining sensitive words, the system can intelligently identify and intercept them during content generation, display, or storage stages to prevent the spread of sensitive information.
Feature Highlights
-
Supports batch import and export, facilitating centralized management of large volumes of sensitive words.
-
Flexible status control, allowing each sensitive word to be individually enabled or disabled.
-
Supports description information, making it easier to record the background and purpose of sensitive word settings.
-
Import template validation mechanism, preventing format errors or duplicate entries during import.
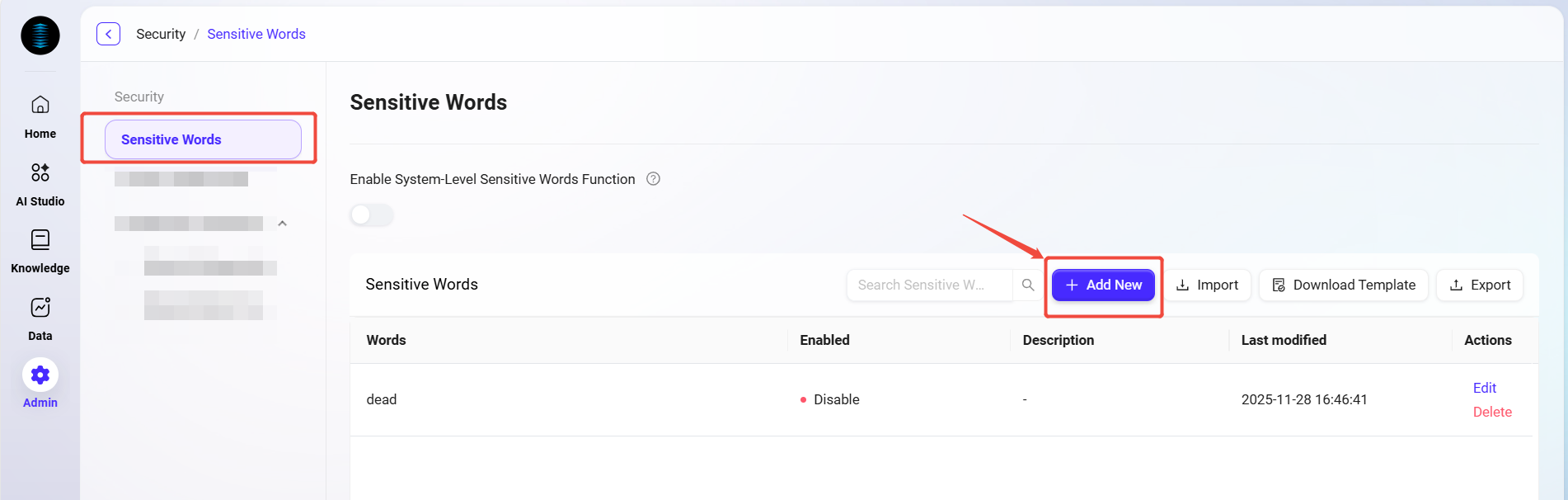
Adding New Sensitive Words
Users can manually add one or multiple sensitive words by following these steps:
-
Navigate to:
Content Security Management -> Sensitive Words -> New. -
In the pop-up window, fill in the following information:
-
Sensitive Word: e.g.,
Text(within 225 characters). -
Enable Status: choose
EnableorDisable. -
Description (optional): additional explanation of the background for adding the sensitive word (within 500 characters).
-
-
Click Save; the sensitive word will take effect immediately or be saved for later use (depending on the enable status).
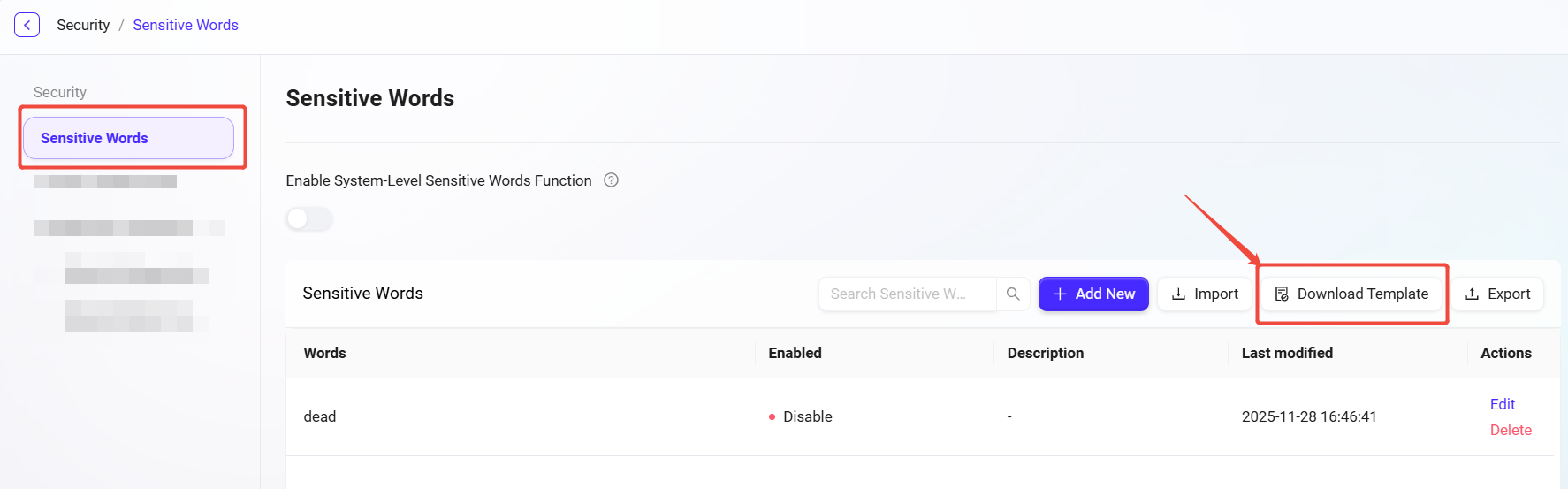
Download Import Template
To facilitate batch management of sensitive words, the system provides a unified import template. The steps are as follows:
-
Navigate to:
Content Security Management -> Sensitive Words -> Download Template. -
The system will automatically download an Excel file, named by default:
Sensitive Words Import Template.xlsx. -
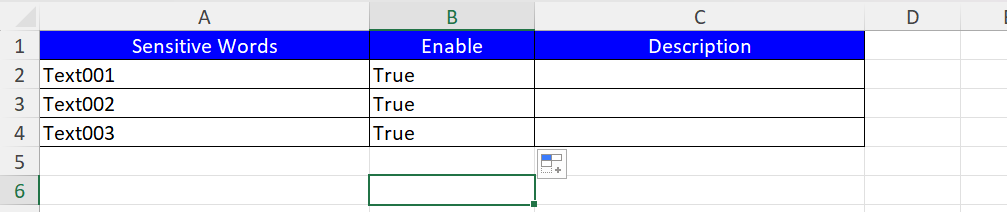
Open the template file and fill in the following fields:
-
Sensitive Word(required) -
Enable(Yes / No) -
Description(optional)
-
-
Save the completed file for import use.
Import Sensitive Words
After preparing the sensitive word template, batch import can be performed as follows:
-
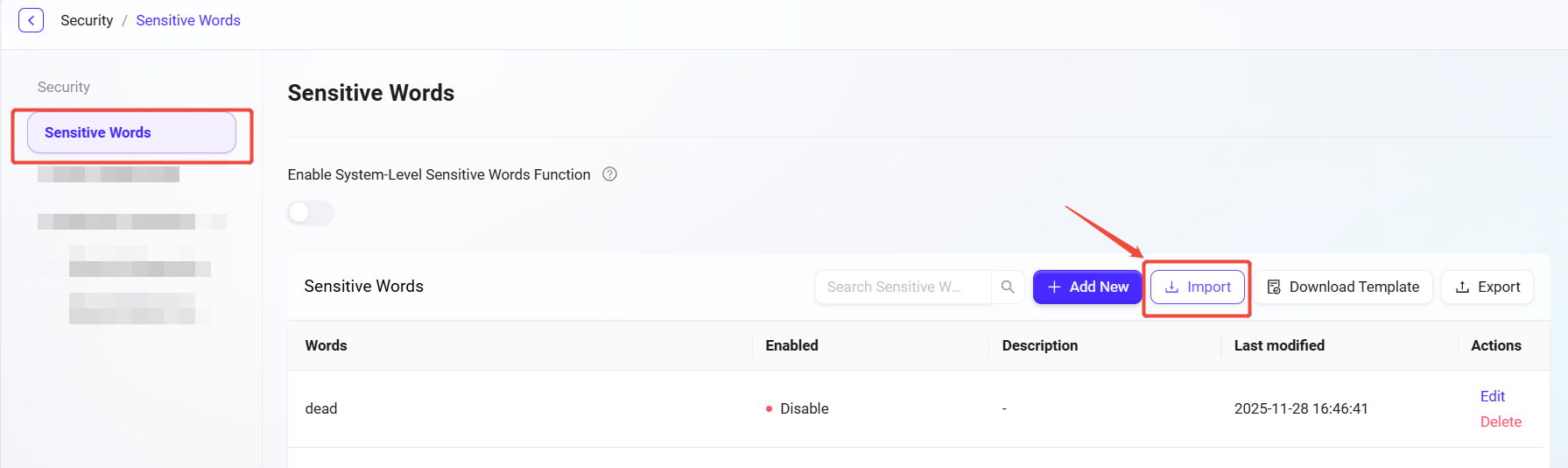
Navigate to:
Content Security Management -> Sensitive Words -> Import. -
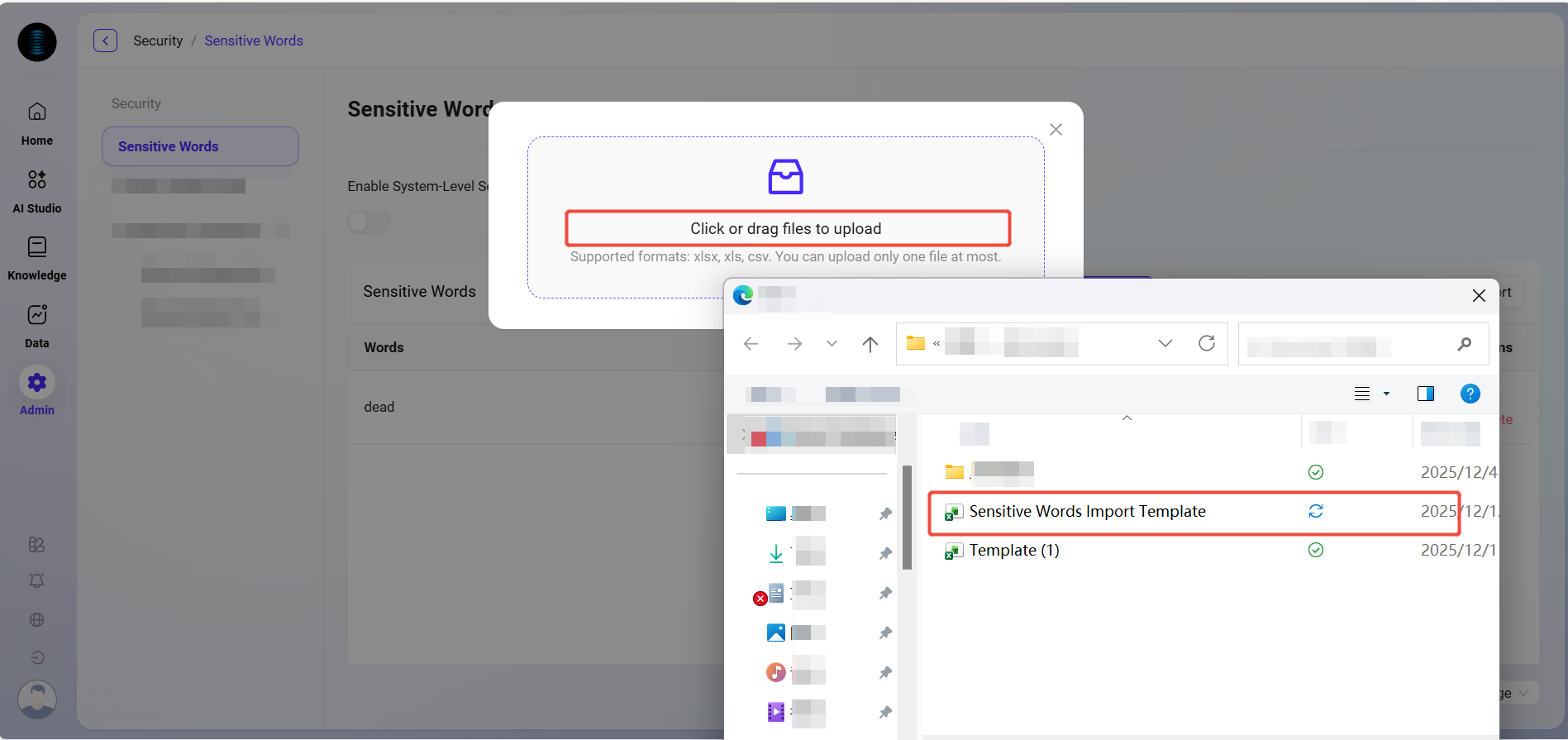
Click the upload area to upload, or drag and drop the template file.
-
The system will automatically validate the content (field completeness, format, duplicates, etc.).
-
After successful import, a "Upload Successful" message will be displayed, and the newly added sensitive words will appear in the list.
⚠️ Supported file formats: xlsx, xls, csv. Only one file can be uploaded at a time. Confirm the format is correct before importing.
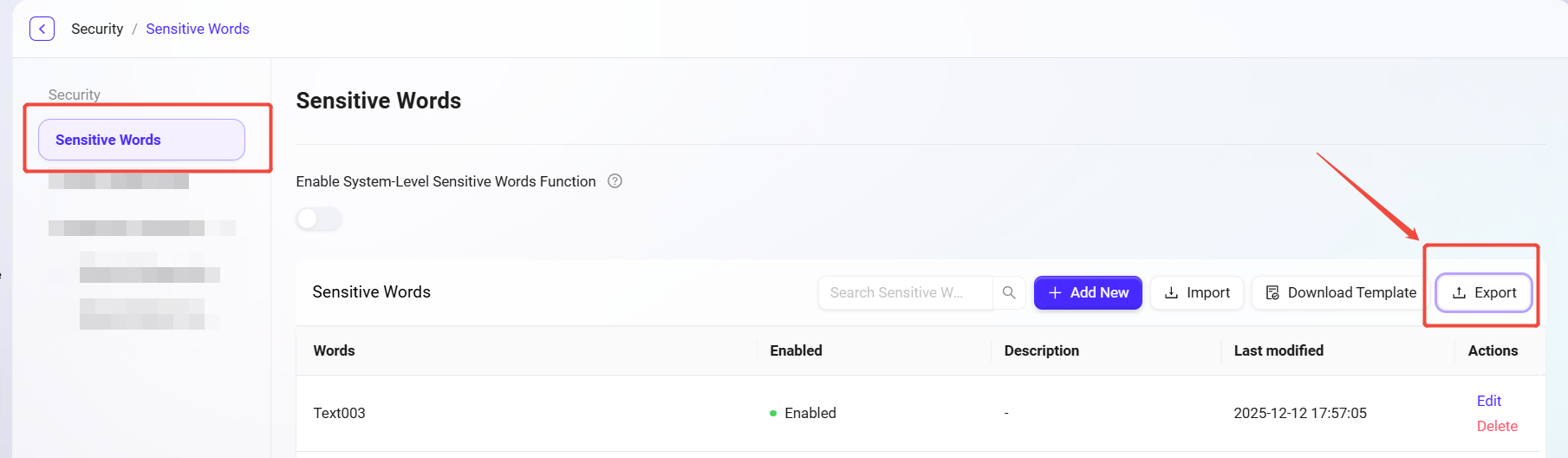
Export Sensitive Words
The platform supports exporting all sensitive words as an Excel file. The steps are as follows:
-
Navigate to:
Content Security Management -> Sensitive Words -> Export. -
After clicking export, the system will automatically download an
.xlsxfile, named by default:Sensitive Words Report.xlsx. -
The report includes the sensitive word itself, enable status, and description information, facilitating archiving and sharing.
Content Review Model
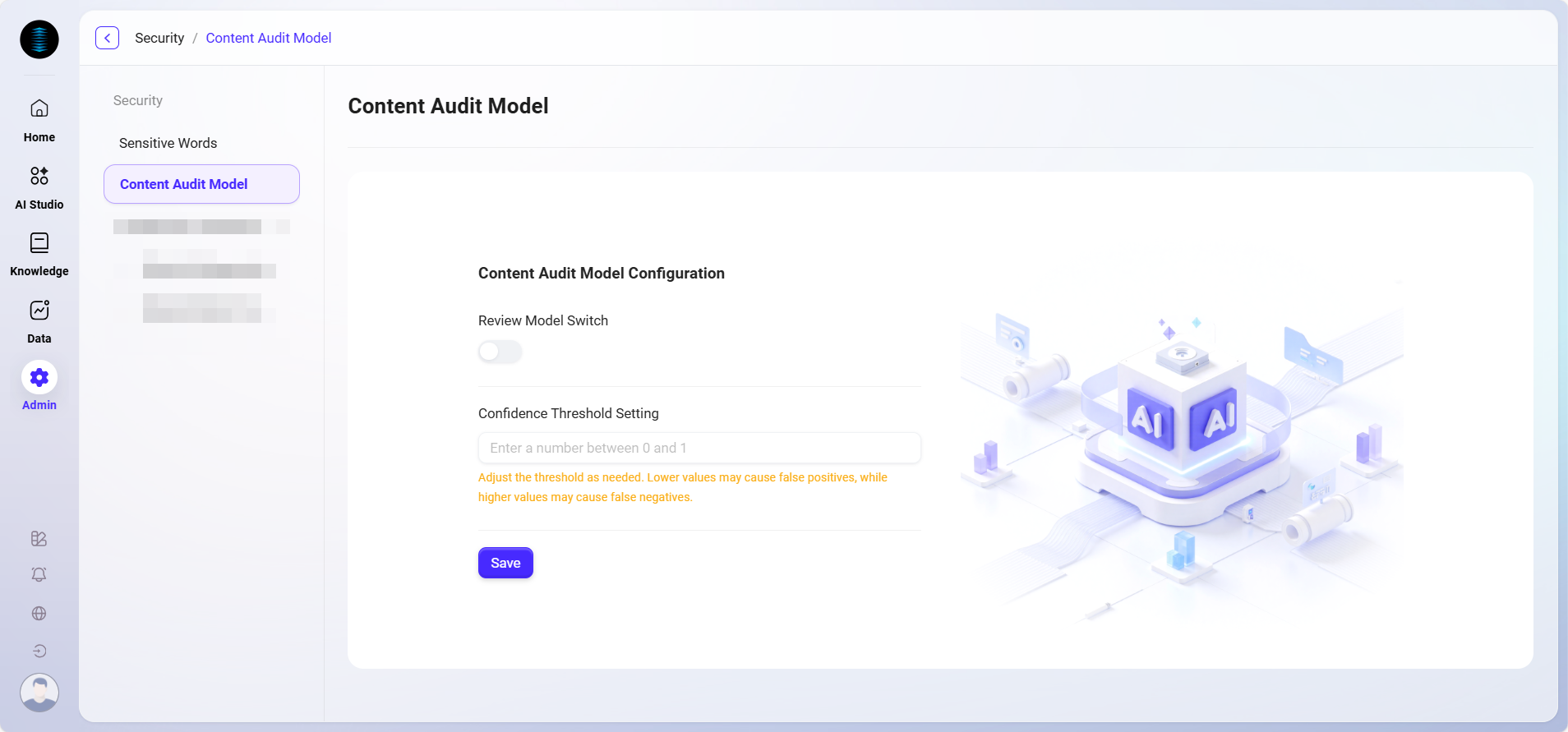
Confidence usually refers to the degree of certainty a model or system has about its prediction results.
In the context of content review models, the confidence threshold setting is an important feature that allows users to define the minimum confidence level the model must reach before marking content as a specific category (such as spam, inappropriate content, etc.). This helps reduce false positives or false negatives depending on the threshold setting.
For example, if the confidence threshold is set to 0.8, the model will only mark content as inappropriate if it is at least 80% confident in its prediction. This ensures that only cases the model is very sure about will be acted upon.
⚠️ This section is currently under development. Stay tuned.
PII Detection and Desensitization
💡 Tip: This feature is only supported in version V4.1 and above
PII (Personally Identifiable Information) detection and desensitization is used to identify and protect data that may expose personal privacy. The system supports identifying various types of data related to specific individuals either alone or combined with other information. Its core function is to ensure data security and privacy compliance.
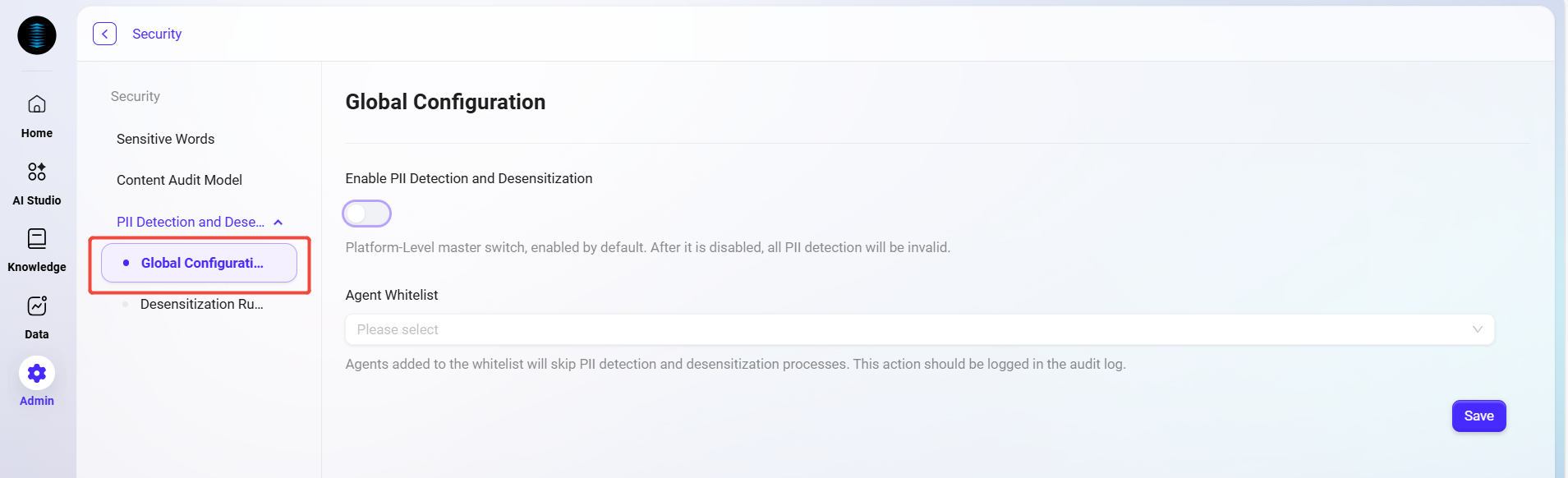
Global Configuration
Interface Description
In the "Administrator Console," navigate to [Content Security Management > PII Detection and Desensitization > Global Configuration] to set unified PII detection policies across the platform.
Configuration Items Description
-
Automatic PII Detection and Desensitization:
-
Platform-level switch, enabled by default.
-
When enabled, the system will automatically identify personal privacy information (such as names, phone numbers, emails, ID numbers, etc.) during Agent interactions and data processing, and perform desensitization.
-
If disabled, all PII detection will be inactive.
-
-
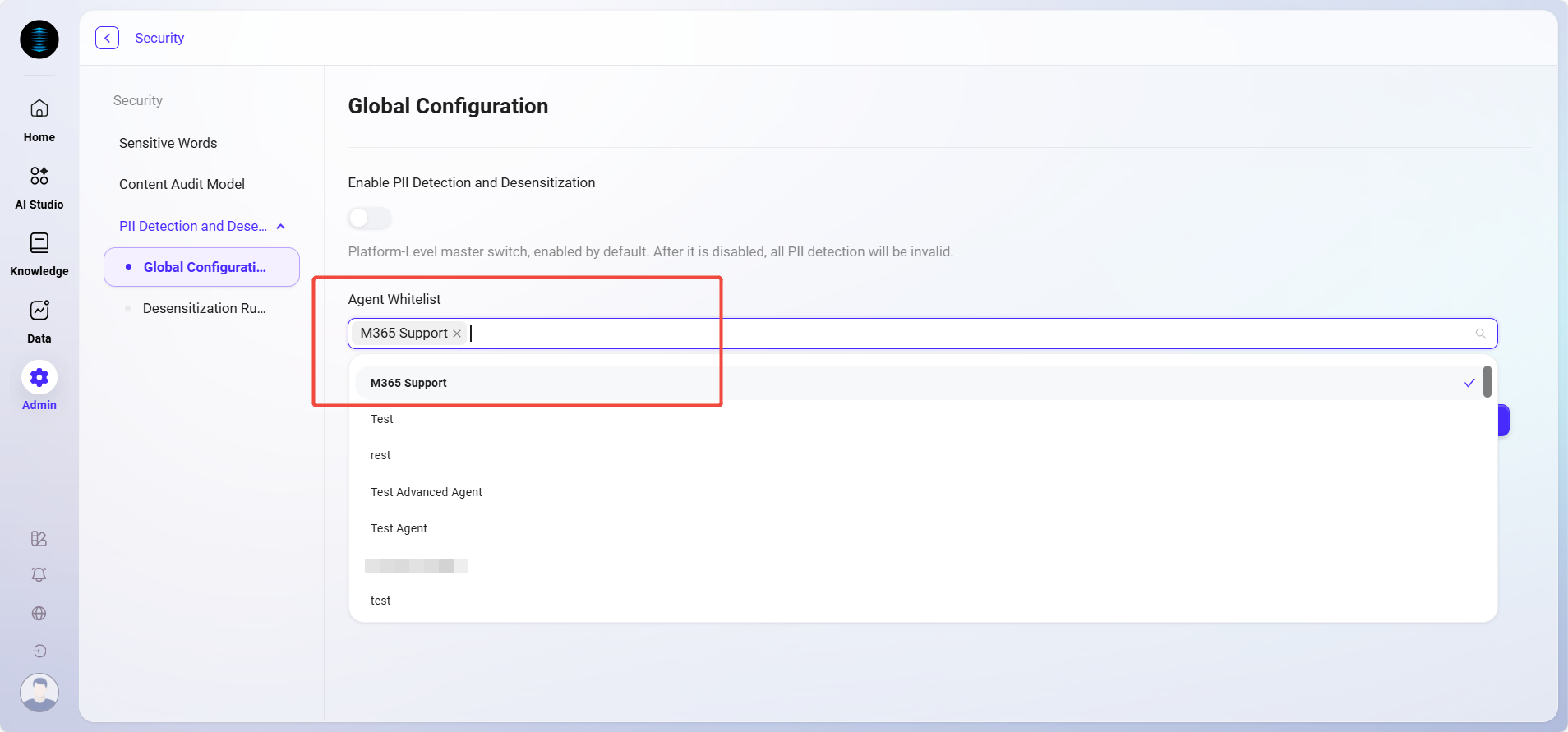
Agent Whitelist:
-
Specific Agents can be added to the whitelist.
-
Agents on the whitelist will bypass PII detection and desensitization processes, but all operations will be recorded in audit logs to ensure security and traceability.
-
Operation Instructions
-
Select the Agents to be excluded from detection in the "Agent Whitelist" dropdown;
-
Toggle the "Automatic PII Detection and Desensitization" switch to enable or disable global detection;
-
Click [Save], and the configuration will take effect immediately.
Functionality
-
Automatically identify and desensitize sensitive personal information to prevent privacy leaks;
-
Supports flexible configuration to meet privacy policies in different business scenarios;
-
Audit logs can trace all configuration changes to ensure security, compliance, and controllability.
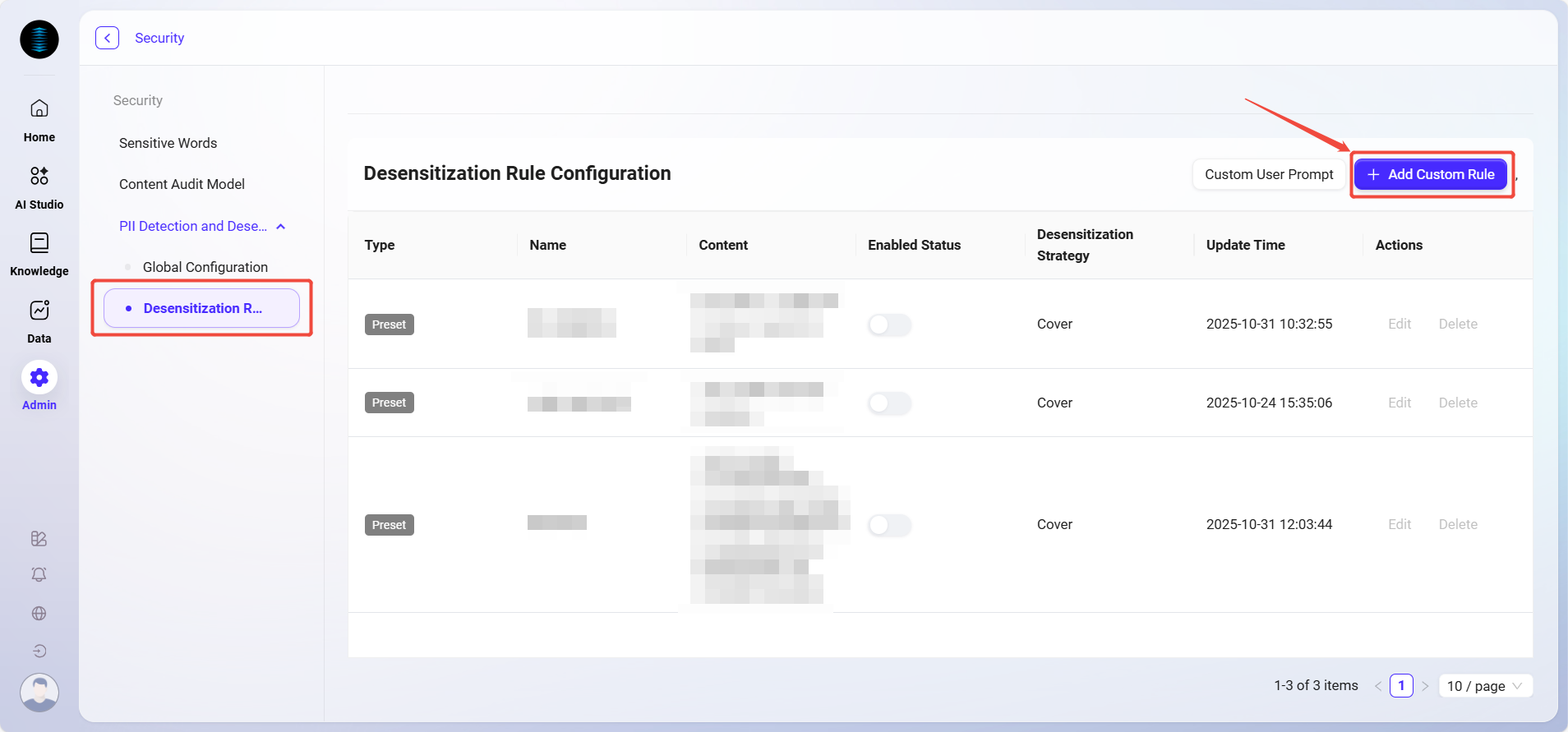
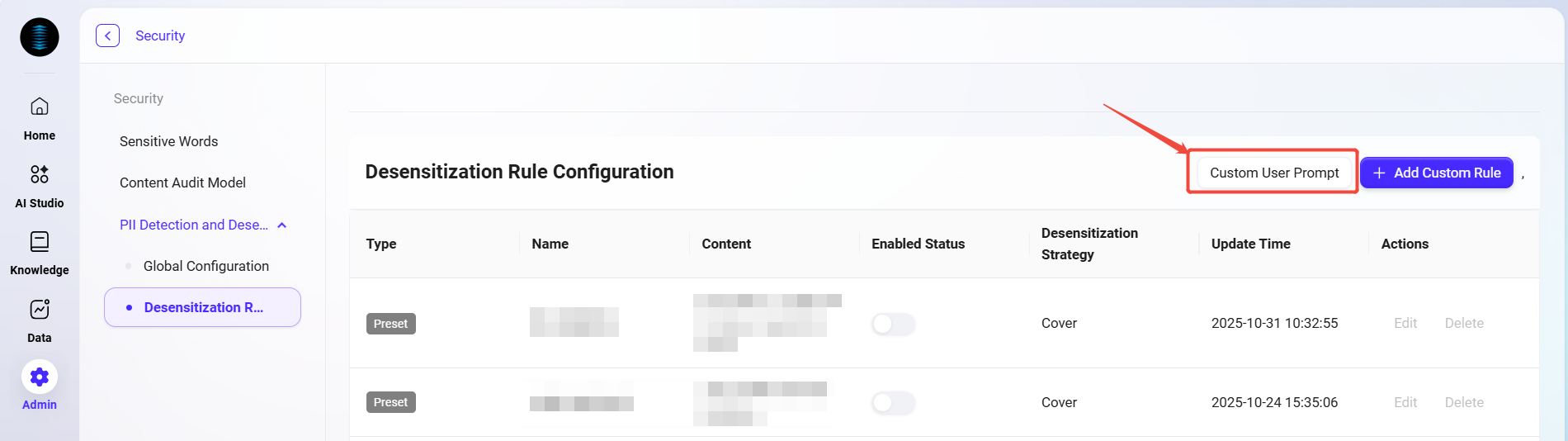
Desensitization Rule Configuration
💡 Tip: This feature is only supported in V4.1 and above
Function Description
"Desensitization Rule Configuration" is used to define the system's handling strategies when personal sensitive information (PII) is detected. By setting different rules and strategies, administrators can flexibly control how the system identifies, prompts, and desensitizes sensitive data, ensuring data compliance and privacy security.
Page Description
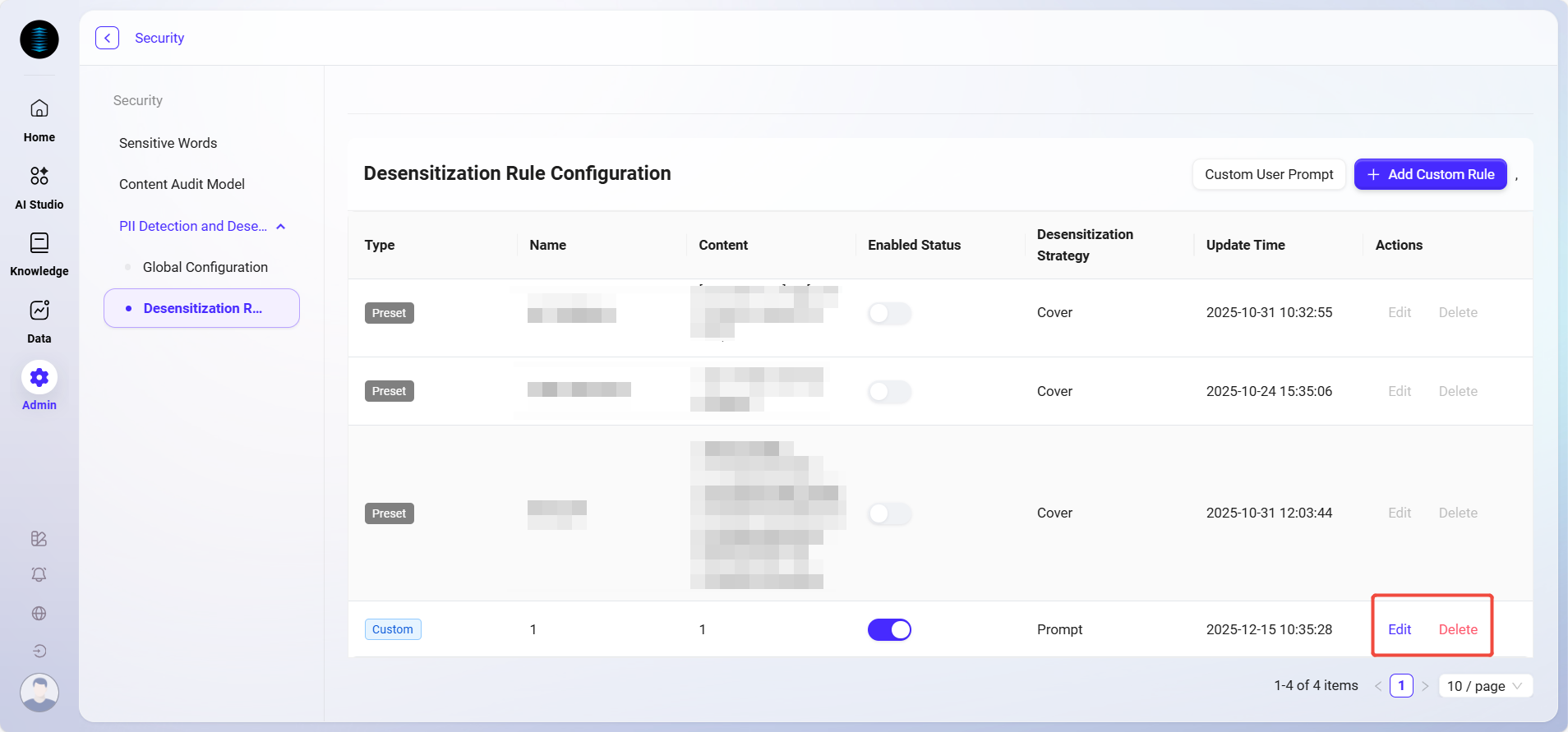
The page displays all desensitization rules configured in the system, including the following information:
-
Rule Type: Distinguishes between system built-in (preset) rules and user-defined rules.
-
Rule Name: The type of sensitive information detected by the rule, such as ID number, mobile phone number, email, etc.
-
Rule Content: The regular expression or detection logic used to match sensitive information.
-
Enable Status: Controls whether the rule is active.
-
Desensitization Strategy: The action the system takes when sensitive information is matched, such as "Mask", "Prompt", "Terminate", "Delete", etc.
-
Update Time: The most recent update time of the rule.
-
Actions: Supports editing or deleting rules.
Configuration Steps
-
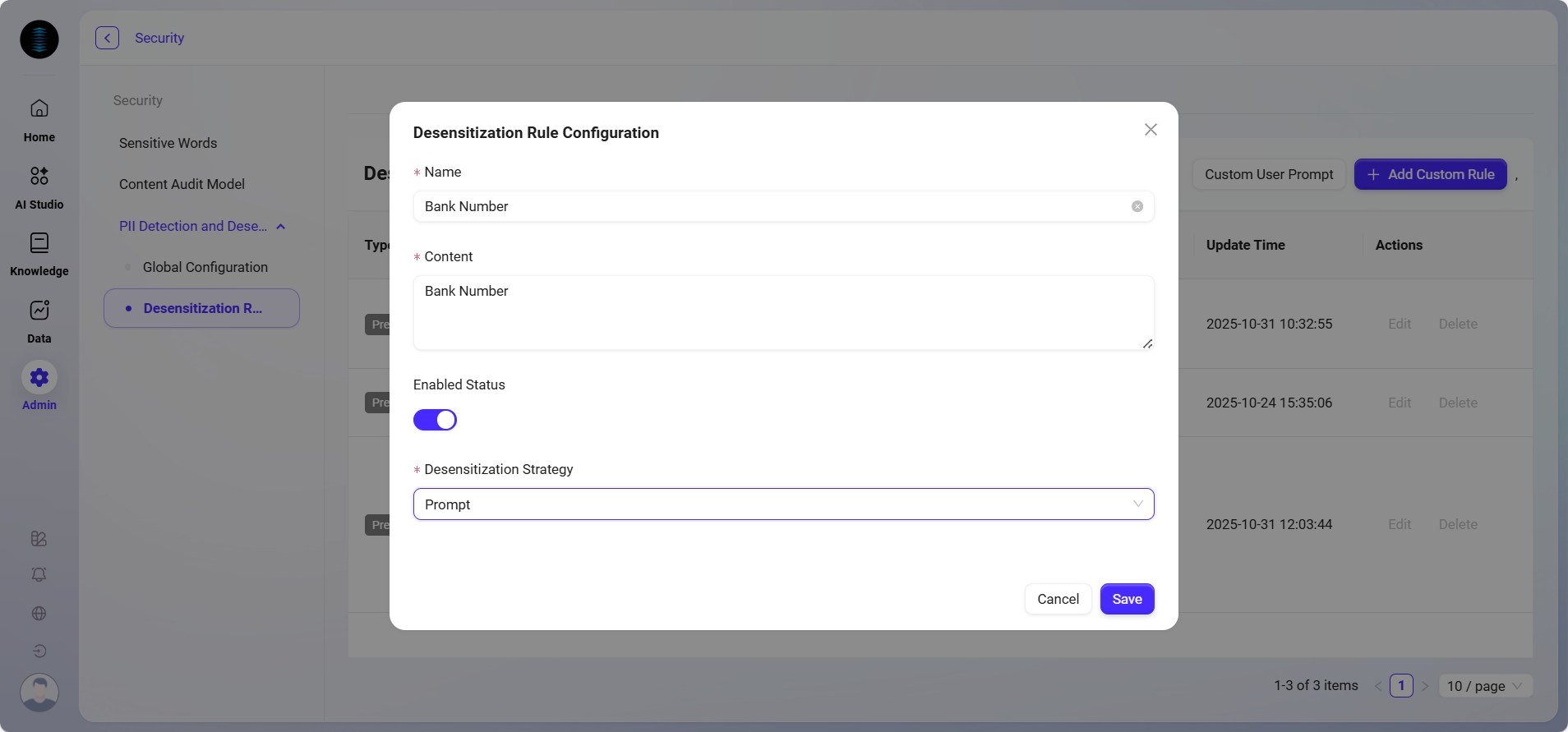
Add Custom Rule
-
Click the "Add Custom Rule" button in the upper right corner of the page;
-
In the pop-up window, fill in the following:
-
Rule Name: Name the rule, such as
Bank Card Number Detection; -
Rule Content: Enter the regular expression used to identify this type of information;
-
Enable Status: Enable immediately or not as needed;
-
Desensitization Strategy: Select the desensitization method from the dropdown (such as "
Mask", "Prompt", "Terminate", "Delete");
-
-
After completing the form, click "Save" and the rule will take effect.
-
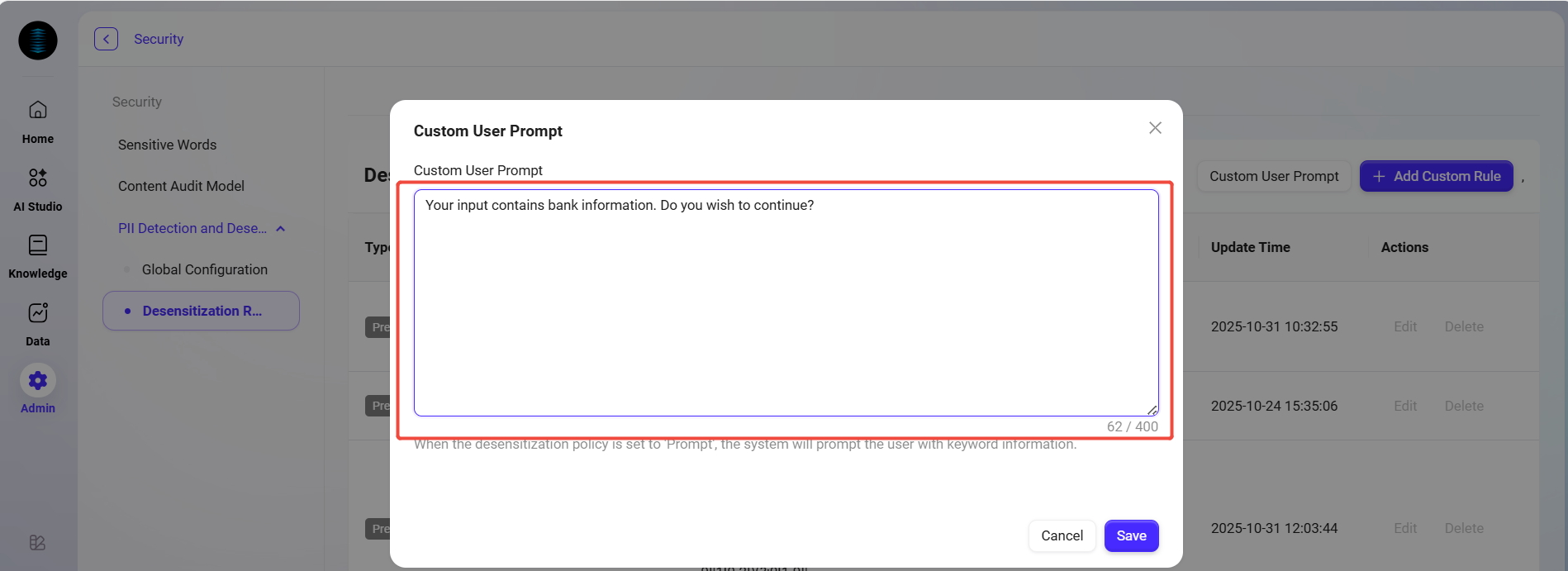
Custom User Prompt
-
When the desensitization strategy is set to "Prompt", you can set the prompt message by clicking "Custom User Prompt" in the upper right corner;
-
Example: "
Your input contains ID information, do you want to continue?"; -
After saving, when the user triggers this rule, the system will pop up a confirmation prompt.
-
Rule Management
-
You can edit the rule content or strategy at any time via "Edit";
-
Unneeded rules can be removed by clicking "Delete".
Usage Example
The system comes with commonly used sensitive information rules (such as ID number, Mainland China mobile phone number, etc.), which administrators can enable directly; you can also add custom rules according to business scenarios, such as detecting email, bank card numbers, or other specific data formats.
