Azure Migrate for VMWare
1 Why use Azure Rapid Discovery and Assessment?
Assess Azure readiness: Assess whether your on-premises machines are suitable for running in Azure.
Get size recommendations: Get size recommendations for Azure VMs based on the performance history of on-premises VMs.
Estimate monthly costs: Get estimated costs for running on-premises machines in Azure.
Get a software inventory: Optionally, applications, roles and features running on VMware VMs can be discovered.
Get dependency information: Optionally, visualize dependencies of on-premises machines to create groups of machines that you will assess and migrate together.
Discover and assess SQL Server: Optionally, discovery and assessment of SQL Server instances and databases running in VMware environment.
Below an overview of the components, the steps, and the communication flows:
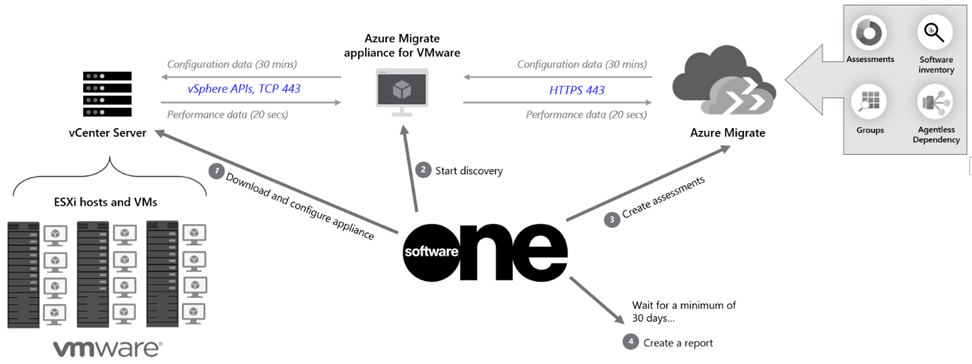
The Azure Rapid Discovery and Assessment service is the first phase in migrating to Microsoft Azure.
2 Requirements Azure Rapid Discovery and Assessment
This engagement supports VMware, Hyper-V, physical servers or other cloud providers like AWS and Google. This document, however, deals with an existing VMware environment and all related requirements.
New or existing Azure subscription in which to create an Azure Migrate project. Optionally, a Free Azure account can be used. However, this can only be used for 30 days, after which a credit card will be required. There are no (PAYG or other) costs involved with an Azure Migrate project.
To create a project and register the Azure Migrate appliance, the following permissions are required:
Entra ID - Permissions to register Microsoft Entra apps are required for this account. The Application Developer role within Entra ID should be sufficient.
Azure RBAC - An account with Owner or Contributor role for the Azure subscription or for a specific resource group in the Azure subscription. This is also a requirement to allow creation of an instance of Azure Key Vault, which is used during agentless server migration at a later stage.
Azure Migrate requires vCenter Server in a VMware environment to perform discovery. Azure Migrate doesn't support discovery of ESXi hosts that aren't managed by vCenter Server.
The VMs that you plan to migrate must be managed by vCenter Server running version 5.5, 6.0, 6.5, 6.7, 7.0 or 8.0. Additionally, you need one ESXi host running at least version 5.5 to deploy the Azure Migrate appliance (VM).
A read-only account in vCenter Server or permissions to create one. Procedure for assigning permissions:
In the menu under Administration, under Access Control, select Global Permissions.
Select the user account and then select Read-only to assign the role to the account. Select OK.
To be able to start discovery of installed applications and agentless dependency analysis, in the menu under Access Control, select Roles. In the Roles pane, under Roles, select Read-only. Under Privileges, select Guest operations. To propagate the privileges to all objects in the vCenter Server instance, select the Propagate to children checkbox.
Before you connect the appliance to vCenter Server, you can limit discovery to vCenter Server datacenters, clusters, a folder of clusters, hosts, a folder of hosts, or individual servers. To set the scope, you assign permissions on the account that the appliance uses to access the vCenter Server. You cannot scope inventory discovery at the vCenter server folder level.
Sufficient permissions and resources on the VMware environment to import an (.ova based) appliance.
The .ova file is approximately 12 GB to download. There should be enough free space to accommodate this file. After downloading it will be uploaded to the VMware environment as part of importing the appliance. The download can be found at Azure Migrate appliance (VMware).
The Azure Migrate appliance requires the following specs:
8 cores/vCPUs.
32 GB RAM (16 GB minimum).
80 GB of disk storage.
External virtual switch. The appliance requires a static or dynamic (DHCP) IP address and needs to connect to Azure through Internet to upload data.
The operating system is Windows Server 2022 (64 bit) with an evaluation license which is valid for 180 days. If the evaluation period is close to expiry and you need to extend the time required for discovery and assessment, we recommend that you download and deploy a new appliance using OVA template, or you activate the operating system license of the appliance server.
If you run the appliance as a VMware VM, you need enough resources within the VMware environment to allocate a VM that meets the requirements.
The appliance checks that the VMware vSphere Virtual Disk Development Kit (VDDK) is installed. VDDK 6.7, 7, or 8 (depending on the compatibility of VDDK and ESXi versions) needs to be installed. Extract the downloaded zipped contents to the specified location on the appliance, as provided in the installation instructions.
The appliance can connect through a proxy to the Internet. Specific requirements to connect via the proxy like username/password of a certificate, needs to be provided by the customer. HTTPS-based proxy servers are not supported by the Azure Migrate appliance.
Check that VMware Tools (version 10.2.1 or later) is installed on each VM you want to analyze.
Windows VMs must have PowerShell version 2.0 or above installed.
It's recommended to create a dedicated domain user account with the required permissions, which is scoped to perform software inventory, agentless dependency analysis and discovery of web app, and SQL Server instances and databases on the desired servers. See next chapters.
The table in Appendix A summarizes the ports needed for Azure Rapid Discovery and Assessment communications.
Other considerations:The Azure Migrate appliance is downloaded, imported, and configured as part of the assessment. It is a connected appliance and will continuously collect performance and other data of VMs. It will automatically reflect any configuration changes that are done to the on-premises environment. The appliance will start collecting performance data from the day it is set up.
The following bullets describe the handling of credentials on the appliance:
All the credentials provided on the appliance configuration manager are stored locally on the appliance server and not sent to Azure.
The credentials stored on the appliance server are encrypted using Data Protection API (DPAPI).
After you have added credentials, appliance attempts to automatically map the credentials to perform discovery on the respective servers.
The appliance uses the credentials automatically mapped on a server for all the subsequent discovery cycles till the credentials can fetch the required discovery data. If the credentials stop working, appliance again attempts to map from the list of added credentials and continue the ongoing discovery on the server.
The domain credentials added will be automatically validated for authenticity against Active Directory. This is to prevent any account lockouts when the appliance attempts to map the domain credentials against discovered servers. The appliance will not attempt to map the domain credentials that have failed validation.
If the appliance cannot map any domain or non-domain credentials against a server, you will see ‘Credentials not available’ status against the server in your project.
You can set up multiple appliances for a single Azure Migrate project. Across all appliances, discovery of up to 50,000 VMs is supported. A maximum of 10,000 VMs running across multiple vCenter Servers can be discovered per appliance. A single appliance can connect to up to 10 vCenter Servers.
If you want to discover a larger environment, you can split the discovery and create multiple projects. Azure Migrate supports up to 20 projects per subscription.
It takes approximately 20-25 minutes for the inventory of discovered servers to appear in the Azure portal.
With continuous profiling of performance data, the Azure Migrate appliance profiles on-premises machines to measure VM performance data. This has almost zero performance impact on the ESXi hosts, as well as on the vCenter Server.
Discovery should run during a representative period of at least 2 weeks, but a full month is preferred. A discovery during the summer holiday period or other national holiday could show results that are not representative for the rest of the year.
3 Optional - Software inventory
In addition to discovering machines and analyzing dependencies, Azure Rapid Discovery and Assessment can discover applications, roles and features running on Windows and Linux servers in your VMware environment. Discovering your software inventory allows you to identify and plan a migration path tailored for your on-premises workloads.
Software inventory is agentless. No agent is installed on VMs, and the appliance doesn't connect directly to the VMs. It uses machine guest credentials and remotely accesses machines using WMI and SSH calls. The software inventory is gathered by connecting to the ESXi hosts through vCenter Server using the VM guest interface (VMware Tools).
The Azure Migrate appliance must be able to connect to TCP port 443 on ESXi hosts running VMs on which you want to perform software inventory. The server running vCenter Server returns an ESXi host connection to download the file that contains the details of the software inventory.
The vCenter Server read-only account used for assessment, needs privileges enabled for Virtual Machines > Guest Operations, to interact with the VM for Software inventory.
The following server credentials are required for this feature:
Use or create a guest user account for Windows VMs and a regular/normal user account (non-sudo access) for all Linux VMs. See Provide server credentials to discover software inventory, dependencies, and SQL Server instances and databases - Azure Migrate | Microsoft Docs for more information.
It's recommended to provide at least one successfully validated domain credential or at least one non-domain credential to initiate software inventory.
You can add multiple domain and non-domain (Windows/Linux) credentials in the appliance configuration manager for software inventory.
If you provided server credentials, Software inventory is automatically initiated when the discovery of servers running vCenter Server is finished. After the initial discovery is complete, software inventory data is collected and sent to Azure once every 24 hours. The duration depends on the number of discovered servers. For 500 servers, it takes approximately one hour for the discovered inventory to appear in the Azure Migrate project in the portal.
You can perform software inventory on up to 10,000 servers running across vCenter Server(s) added to each Azure Migrate appliance.
Software inventory also identifies the SQL Server instances running in your VMware, Microsoft Hyper-V and Physical/ Bare-metal environments as well as IaaS services of other public cloud. For the appliance to gather additional configuration and performance data of SQL Server instances and databases, it needs Windows authentication or SQL Server authentication credentials on the appliance. See chapter 5.
The software inventory will be delivered in Excel (.xlsx) format. The Software Inventory sheet displays all the applications, roles and features discovered across all the servers that could be accessed.
4 Optional - Dependency analysis (agentless)
Dependency analysis (visualization) in Azure Migrate allows you to view network dependencies of machines and identify related machines that needed to be migrated together to Azure. This functionality is useful in scenarios where you are not completely aware of the machines that constitute your application and need to be migrated together to Azure.
Dependency analysis is agentless. No agent is installed on VMs, and the appliance doesn't connect directly to the VMs. It uses machine guest credentials and remotely accesses machines using WMI and SSH calls. The software inventory is gathered by connecting to the ESXi hosts through vCenter Server using the VM guest interface (VMware Tools).
The Azure Migrate appliance must be able to connect to TCP port 443 on ESXi hosts running VMs on which you want to perform Dependency analysis. The server running vCenter Server returns an ESXi host connection to download the file containing the dependency data.
The vCenter Server read-only account used for assessment, needs privileges enabled for Virtual Machines > Guest Operations, to interact with the VM for Software inventory.
Supported Windows operating systems:
Windows Server 2008 (R2) and above
Supported Linux operating systems:
Red Hat Enterprise Linux 5.1, 5.3, 5.11, 6.x, 7.x, 8.x
Ubuntu 12.04, 14.04, 16.04, 18.04, 20.04
OracleLinux 6.1, 6.7, 6.8, 6.9, 7.2, 7.3, 7.4, 7.5, 7.6, 7.7, 7.8, 7.9, 8, 8.1, 8.3, 8.5
SUSE Linux 10, 11 SP4, 12 SP1, 12 SP2, 12 SP3, 12 SP4, 15 SP2, 15 SP3
Debian 7, 8, 9, 10, 11
Dependency analysis needs a vCenter Server account with at least read-only access and privileges enabled for Virtual Machines > Guest Operations to interact with the servers.
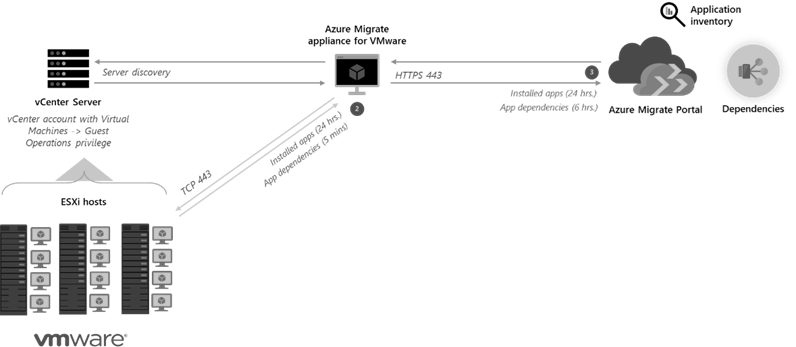
For dependency analysis on Windows, the Azure Migrate appliance needs one of the following accounts for access:
Domain administrator account
Local admin account (per VM)
For dependency analysis on Linux machines one of the following accounts is required for access:
A sudo user account with permissions to execute ls and netstat commands. If you're providing a sudo user account, ensure that you enable NOPASSWD for the account to run the required commands without prompting for a password every time a sudo command is invoked.
Alternatively, you can create a user account that has the CAP_DAC_READ_SEARCH and CAP_SYS_PTRACE permissions on /bin/netstat and /bin/ls files set by using the following commands:
sudo setcap CAP_DAC_READ_SEARCH,CAP_SYS_PTRACE=ep /bin/ls
sudo setcap CAP_DAC_READ_SEARCH,CAP_SYS_PTRACE=ep /bin/netstat
See Provide server credentials to discover software inventory, dependencies, web apps, and SQL Server instances and databases for more information about credentials.
After the server discovery is complete, appliance initiates the discovery of installed applications, roles, and features (software inventory) on the servers. During software inventory, the discovered servers are validated to check if they meet the prerequisites and can be enabled for agentless dependency analysis.
The dependency data available will be exported and downloaded in a CSV format. The downloaded file contains the dependency data across all VMs accessible for dependency analysis.
In an Azure Migrate project, dependency data collection can be enabled concurrently for 1,000 servers across multiple vCenter Servers.
5 Optional - SQL Server instance and database discovery
Assess on-premises databases and evaluate compatibility for migration to Azure SQL Database or to SQL Managed Instance.
Currently supported only for servers running SQL Server in your VMware environment. From a single appliance, you can discover up to 750 SQL Server instances or 15,000 SQL databases, whichever is less.
Azure Migrate requires a Windows user account that is a member of the sysadmin server role. As an alternative, although more complex, a least privilege account can be created and configured. More information about this option can be found at Create a custom account with minimal metadata for discovery and assessment and VMware server discovery support in Azure Migrate and Modernize.
Supported
Windows Server 2008 and later.
SQL Server 2008 and later.
Enterprise, Standard, Developer and Express editions.
Only SQL Server Database Engine is supported. No support for Discovery of SQL Server Reporting Services (SSRS), SQL Server Integration Services (SSIS), and SQL Server Analysis Services (SSAS).
Both Windows and SQL Server authentication are supported. You can provide credentials of both authentication types in the appliance configuration manager. To discover SQL Server instances and databases, you can provide domain credentials if you have configured Windows authentication mode on your SQL Servers.
Discovery of standalone, highly available, and disaster-protected SQL deployments is supported. Discovery of high-availability disaster recovery SQL deployments powered by Always On failover cluster Instances and Always On availability groups is also supported.
Not supported
Linux.
Appliance can connect to only those SQL Server instances to which it has network line of sight, whereas software inventory by itself may not need network line of sight.
The assessment only includes databases that are in online status. In case the database is in any other status, the assessment ignores the readiness, sizing, and cost calculation for such databases. In case you wish you assess such databases, please change the status of the database, and recalculate the assessment in some time.
Software inventory identifies the SQL Server instances that are running on the servers. Using the information it collects, the appliance attempts to connect to the SQL Server instances through the Windows authentication credentials or the SQL Server authentication credentials that are provided on the appliance. Then, it gathers data on SQL Server databases and their properties. The SQL Server discovery is performed once every 24 hours. Hence any change to the properties of the SQL Server instance and databases such as database status, compatibility level etc. can take up to 24 hours to update on the portal.

6 Azure Migrate Private Link support
By default, Azure Migrate uses a secure connection over the internet to discover, assess, and migrate servers. Azure Migrate Private Link support allows you to connect privately and securely to the Azure Migrate service over an ExpressRoute private peering (or a site-to-site VPN connection).
With the Azure Migrate Private Link support, you can:
Execute faster: Leverage existing ExpressRoute private peering circuits for greater migration velocity.
Be compliant: Adhere to organizational policies and requirements to not traverse public endpoints.
Be secure: Achieve additional network-level protection and guard against data exfiltration risks.
The ExpressRoute or site-to-site VPN gateway should be reachable from the virtual network where the private endpoint resides. You might need about 15 IP addresses in the virtual network. Additional DNS configuration and a managed identity are required for this setup.
In most cases, however, you will not be able to disable public access entirely, as some features still will need that. For example, some migration tools might not be able to upload usage data to the Azure Migrate project if public network access is disabled. You can't change the connectivity method to private endpoint connectivity after the Azure Migrate has been created.
Configuration of Private Link and the use of it with Azure Migrate is out of scope of this project.
7 Azure Arc support
Azure Arc-enabled servers let you manage Windows & Linux physical servers and VMs hosted outside of Azure, on your corporate network, or other cloud provider. Azure Arc allows you to manage your hybrid IT estate with a single pane of glass by extending the Azure management experience to your on-premises servers that are not ideal candidates for migration. By projecting your existing non-Azure and/or on-premises resources into Azure Resource Manager, it offers the following Azure Arc control plane functionality at no extra cost:
Resource organization through Azure management groups and tags
Searching and indexing through Azure Resource Graph
Access and security through Azure Role-based access control (RBAC)
A unified experience viewing your Azure Arc-enabled resources, whether you are using the Azure portal, the Azure CLI, Azure PowerShell, or Azure REST API.
Automation through templates and extensions
Any additional Azure service that is used on Azure Arc-enabled servers, such as Microsoft Defender for Cloud or Azure Monitor, will be charged as per the pricing for that service. Keep in mind that this can lead to additional costs; this is highly dependent on the number of servers you onboard.
For the purposes of Azure Arc, these machines hosted outside of Azure are considered hybrid machines. To connect hybrid machines to Azure, you install the Azure Arc Hybrid Connected Machine agent on each VM. It is possible to onboard on-premises VMware VMs to Azure Arc for Azure Management using the Azure Migrate appliance.
When configuring the Azure connected machine agent to communicate with Azure through a private link, some endpoints must still be accessed through the internet.
Some additional steps are required to enable this onboard feature and by default, SoftwareOne does not include this option for the Azure Migrate Discover and Access. However, there is always room for discussion to add this option to the scope.
8 Collected data and residency
The appliance collects metadata and performance data. Dependency analysis, application discovery and SQL data discovery are optional. More information on what metadata is gathered, can be found at Discovered metadata - Azure Migrate | Microsoft Learn. Microsoft doesn't use this data in any license compliance audit.
This data is uploaded to Azure through a secure connection over the internet (or ExpressRoute).
Azure Migrate only collects metadata about VMs in scope and allows you to select an Azure geography where the discovered metadata would be stored. The project and related resources are created in one of the regions in the geography, as allocated by the Azure Migrate service. For the geography Europe, this could either be North Europe or West Europe. By using a custom option, we can even force the location to be West Europe.
Azure Migrate doesn't move or store customer data outside of the region allocated, guaranteeing data residency and resiliency in the same geography.
Although you can only create projects in specific geographies (see Azure Migrate support matrix - Azure Migrate | Microsoft Learn for an updated list), you can assess or migrate servers for other target locations. The project geography is only used to store the discovered metadata.
Data collection frequency:
Configuration metadata is collected and sent every 15 minutes.
Performance Software inventory data is sent to Azure once every 24 hours. metadata is collected every 50 minutes to send a data point to Azure.
Software inventory data is sent to Azure once every 24 hours.
Agentless dependency data is collected every 5 minutes, aggregated on appliance and sent to Azure every 6 hours.
The SQL Server configuration data is updated once every 24 hours and the performance data is captured every 30 seconds.
The web apps configuration data is updated once every 24 hours. Performance data is not captured for web apps.
9 Appendix A - Communication ports
Component Communicates with Details
Azure Migrate appliance Azure Migrate Service (Internet) Outbound connections on port 443 (HTTPS) to send discovery and performance metadata to the Azure Migrate project.
Azure Migrate appliance vCenter server Inbound connections on TCP port 443 to allow the appliance to collect configuration and performance metadata for assessments.
The appliance connects to vCenter on port 443 by default. If vCenter Server listens on a different port, you can modify the port when you set up discovery.
Azure Migrate appliance ESXi host(s) For discovery of installed applications or agentless dependency analysis, the appliance connects to ESXi hosts on TCP port 443 to discover software inventory and dependencies on the servers.
This is also a prerequisite for the SQL Assessment, as it provides the necessary data to populate the list of SQL instances.
Administrator workstation(s) Azure Migrate appliance Inbound connections on port 44368 to remotely access the appliance management app using the URL: <https://<appliance-ip-or-name>>:44368.
Administrator workstation(s) Azure Migrate appliance RDP over port 3389 (optional) to allow remote desktop connections to the appliance.
10 Appendix B - Restrict URLs
Some Azure Migrate components need connectivity to specific URLs. To increase security, communication can be limited to these specific URLs.
Azure Migrate appliance
The Azure Migrate appliance needs connectivity to the internet to be able to discover VMs. The connectivity to internet is validated by connecting to a list of Azure Public Cloud URLs as given in the following table.
URL Details
*.portal.azure.com Checks connectivity with the Azure service and time synchronization.
*.windows.net
*.msftauth.net
*.msauth.net
*.microsoft.com
*.live.com
*.office.com
*.microsoftonline.com
*.microsoftonline-p.com
*.microsoftazuread-sso.com Log in to your Azure subscription. Create Azure AD apps for the appliance to communicate with the Azure Migrate service.
management.azure.com Used for resource deployments and management operations
*.services.visualstudio.com Upload appliance logs used for internal monitoring.
*.vault.azure.net Manage secrets in the Azure Key Vault. Note: Ensure machines to replicate have access to this.
*.servicebus.windows.net Communication between the appliance and the Azure Migrate service.
*.discoverysrv.windowsazure.com
*.migration.windowsazure.com Connect to Azure Migrate service URLs.
aka.ms/* Allow access to these links; used to download and install the latest updates for appliance services.
http://download.microsoft.com/download Allows downloads from the Microsoft Download center.
If you have an intercepting proxy, you might need to import the server certificate from the proxy server to the appliance. If you're using a URL-based proxy, allow access to the URLs in the table, making sure that the proxy resolves any CNAME records received while looking up the URLs.
Additional ports are required when support for Private Link or Azure Arc is enabled.
Disclaimer
This publication contains confidential and proprietary information that is protected by copyright. SoftwareOne reserves all rights thereto. SoftwareOne shall not be liable for obvious typing and arithmetic errors in any document provided by SoftwareOne. Liability for damages directly and indirectly associated with the supply or use of this document is limited in accordance with the supply or use of this document is excluded as far as legally permissible.
The SoftwareOne Azure Migrate prerequisite information presented herein is intended exclusively as a guide to support the offering of SoftwareOne. It must not be copied, reproduced, passed to third parties or used for engineering purposes without the express permission of SoftwareOne.
Copyright © 2024 by SoftwareOne. All rights reserved. SoftwareOne is a registered trademark of SoftwareOne AG. All other trademarks, service marks or trade names appearing herein are the property of their respective owners.
